co.bw
Updated:
2021-05-20 12:50:09 UTC (1712 days ago)
Go to most recent »
Notices
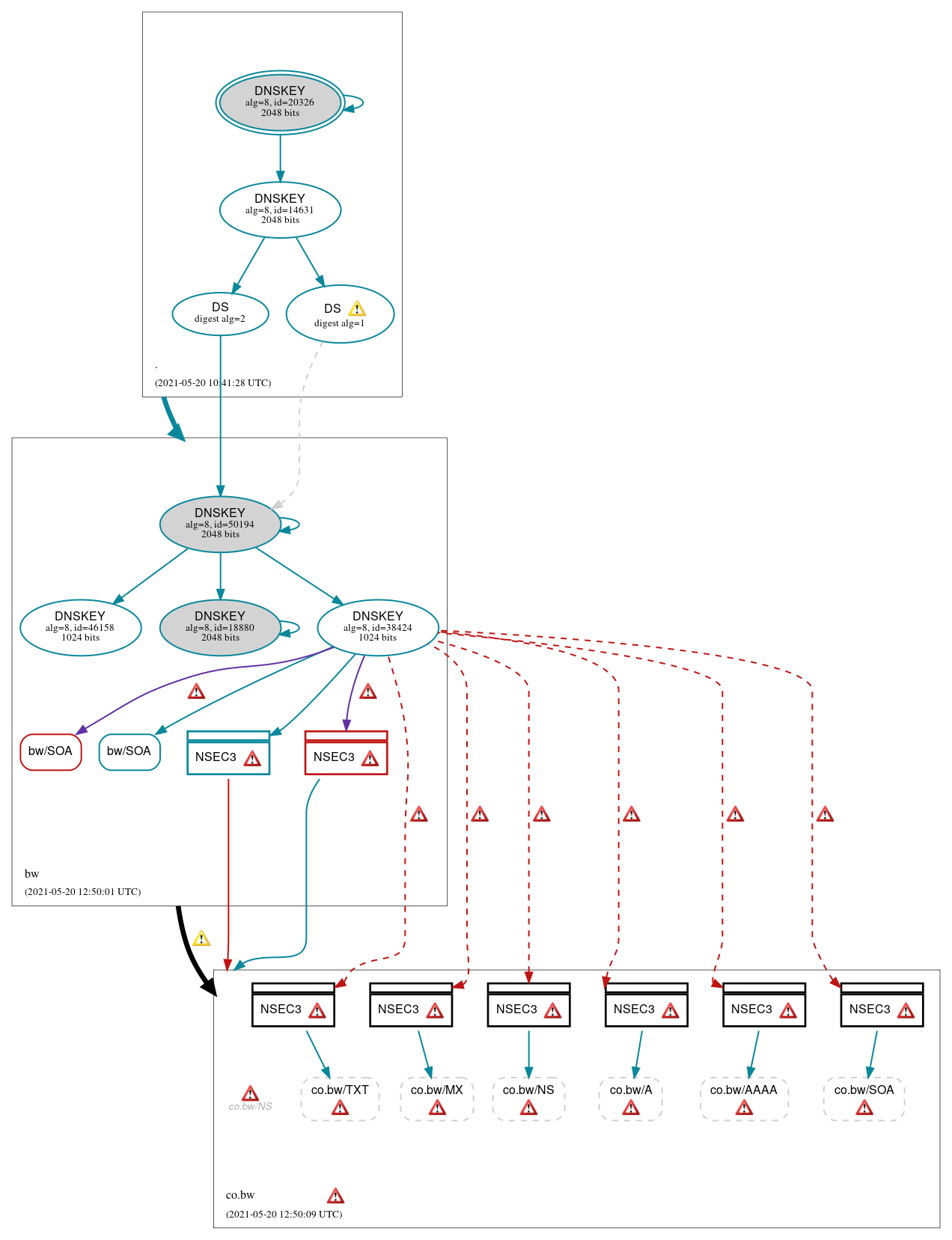
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (1)
- bw/SOA
Insecure (6)
- co.bw/A (NODATA)
- co.bw/AAAA (NODATA)
- co.bw/MX (NODATA)
- co.bw/NS (NODATA)
- co.bw/SOA (NODATA)
- co.bw/TXT (NODATA)
Secure (1)
- bw/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Bogus (1)
- NSEC3 proving non-existence of co.bw/DS
Insecure (6)
- NSEC3 proving non-existence of co.bw/A
- NSEC3 proving non-existence of co.bw/AAAA
- NSEC3 proving non-existence of co.bw/MX
- NSEC3 proving non-existence of co.bw/NS
- NSEC3 proving non-existence of co.bw/SOA
- NSEC3 proving non-existence of co.bw/TXT
Secure (9)
- ./DNSKEY (alg 8, id 14631)
- ./DNSKEY (alg 8, id 20326)
- NSEC3 proving non-existence of co.bw/DS
- bw/DNSKEY (alg 8, id 18880)
- bw/DNSKEY (alg 8, id 38424)
- bw/DNSKEY (alg 8, id 46158)
- bw/DNSKEY (alg 8, id 50194)
- bw/DS (alg 8, id 50194)
- bw/DS (alg 8, id 50194)
 Delegation status
Delegation status
Insecure (1)
- bw to co.bw
Secure (1)
- . to bw
 Notices
Notices
Errors (38)
- NSEC3 proving non-existence of co.bw/A: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/A: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/AAAA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/AAAA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: The NS bit was not set in the bitmap of the NSEC3 RR corresponding to the delegated name (co.bw). See RFC 5155, Sec. 8.9.
- NSEC3 proving non-existence of co.bw/DS: The NS bit was not set in the bitmap of the NSEC3 RR corresponding to the delegated name (co.bw). See RFC 5155, Sec. 8.9.
- NSEC3 proving non-existence of co.bw/MX: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/MX: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/NS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/NS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/SOA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/SOA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/TXT: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/TXT: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- RRSIG NSEC3 proving non-existence of co.bw/A alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (co.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of co.bw/AAAA alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (co.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of co.bw/DS alg 8, id 38424: The Signature Expiration field of the RRSIG RR (2020-11-01 16:15:10+00:00) is 199 days in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of co.bw/MX alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (co.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of co.bw/NS alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (co.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of co.bw/SOA alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (co.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of co.bw/TXT alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (co.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG bw/SOA alg 8, id 38424: The Signature Expiration field of the RRSIG RR (2020-11-04 04:44:35+00:00) is 197 days in the past. See RFC 4035, Sec. 5.3.1.
- co.bw zone: The server(s) did not respond authoritatively for the namespace. See RFC 1035, Sec. 4.1.1. (2001:43f8:120::72)
- co.bw/A (NODATA): An SOA RR with owner name (bw) not matching the zone name (co.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, 204.61.216.70, 2001:500:14:6070:ad::1, 2c0f:ff00:1:3::226, UDP_-_EDNS0_4096_D_KN)
- co.bw/AAAA (NODATA): An SOA RR with owner name (bw) not matching the zone name (co.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, 204.61.216.70, 2001:500:14:6070:ad::1, 2c0f:ff00:1:3::226, UDP_-_EDNS0_4096_D_KN)
- co.bw/MX (NODATA): An SOA RR with owner name (bw) not matching the zone name (co.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, 204.61.216.70, 2001:500:14:6070:ad::1, 2c0f:ff00:1:3::226, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- co.bw/NS (NODATA): An SOA RR with owner name (bw) not matching the zone name (co.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, 204.61.216.70, 2001:500:14:6070:ad::1, 2c0f:ff00:1:3::226, UDP_-_EDNS0_4096_D_KN)
- co.bw/NS: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (168.167.168.37, 2c0f:ff00:0:6::3, 2c0f:ff00:0:6::5, UDP_-_NOEDNS_)
- co.bw/SOA (NODATA): An SOA RR with owner name (bw) not matching the zone name (co.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, 204.61.216.70, 2001:500:14:6070:ad::1, 2c0f:ff00:1:3::226, TCP_-_EDNS0_4096_D_N, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_4096_D_KN_0x20)
- co.bw/TXT (NODATA): An SOA RR with owner name (bw) not matching the zone name (co.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, 204.61.216.70, 2001:500:14:6070:ad::1, 2c0f:ff00:1:3::226, UDP_-_EDNS0_4096_D_KN)
- co.bw/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- co.bw/DS has errors; select the "Denial of existence" DNSSEC option to see them.
- 8oqkvb450c.co.bw/A has errors; select the "Denial of existence" DNSSEC option to see them.
- co.bw/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (25)
- NSEC3 proving non-existence of co.bw/A: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/A: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/AAAA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/AAAA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/MX: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/MX: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/NS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/NS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/SOA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/SOA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/TXT: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of co.bw/TXT: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- bw to co.bw: The following NS name(s) were found in the delegation NS RRset (i.e., in the bw zone), but not in the authoritative NS RRset: dns1.nic.net.bw, pch.nic.net.bw, ns-bw.afrinic.net See RFC 1034, Sec. 4.2.2.
- bw/DS (alg 8, id 50194): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bw/DS (alg 8, id 50194): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bw/DS (alg 8, id 50194): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- bw/DS (alg 8, id 50194): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- co.bw/DNSKEY has warnings; select the "Denial of existence" DNSSEC option to see them.
- co.bw/DS has warnings; select the "Denial of existence" DNSSEC option to see them.
- 8oqkvb450c.co.bw/A has warnings; select the "Denial of existence" DNSSEC option to see them.
- co.bw/CNAME has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.