www.dibbs.bsm.dla.mil
Updated:
2020-07-08 22:52:53 UTC (1644 days ago)
Go to most recent »
Notices
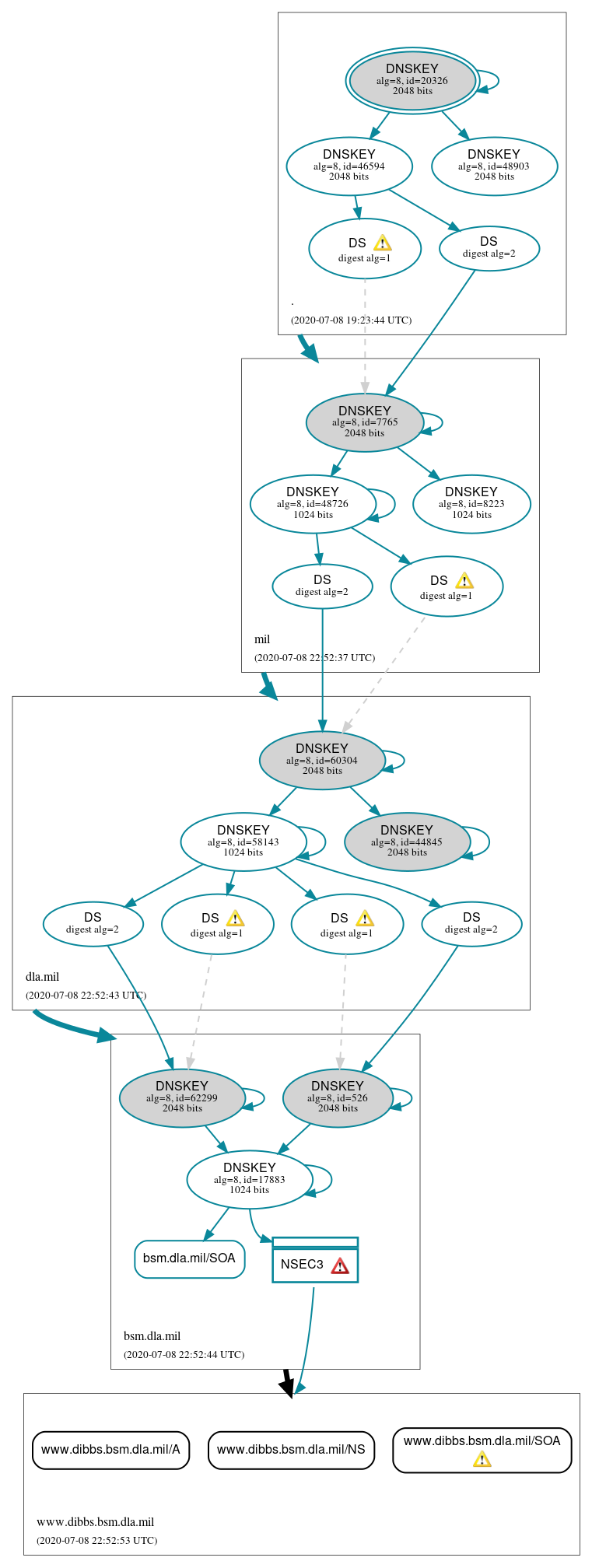
DNSSEC Authentication Chain
 RRset status
RRset status
Insecure (3)
- www.dibbs.bsm.dla.mil/A
- www.dibbs.bsm.dla.mil/NS
- www.dibbs.bsm.dla.mil/SOA
Secure (1)
- bsm.dla.mil/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (21)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 46594)
- ./DNSKEY (alg 8, id 48903)
- NSEC3 proving non-existence of www.dibbs.bsm.dla.mil/DS
- bsm.dla.mil/DNSKEY (alg 8, id 17883)
- bsm.dla.mil/DNSKEY (alg 8, id 526)
- bsm.dla.mil/DNSKEY (alg 8, id 62299)
- bsm.dla.mil/DS (alg 8, id 526)
- bsm.dla.mil/DS (alg 8, id 526)
- bsm.dla.mil/DS (alg 8, id 62299)
- bsm.dla.mil/DS (alg 8, id 62299)
- dla.mil/DNSKEY (alg 8, id 44845)
- dla.mil/DNSKEY (alg 8, id 58143)
- dla.mil/DNSKEY (alg 8, id 60304)
- dla.mil/DS (alg 8, id 60304)
- dla.mil/DS (alg 8, id 60304)
- mil/DNSKEY (alg 8, id 48726)
- mil/DNSKEY (alg 8, id 7765)
- mil/DNSKEY (alg 8, id 8223)
- mil/DS (alg 8, id 7765)
- mil/DS (alg 8, id 7765)
 Delegation status
Delegation status
Insecure (1)
- bsm.dla.mil to www.dibbs.bsm.dla.mil
Secure (3)
- . to mil
- dla.mil to bsm.dla.mil
- mil to dla.mil
 Notices
Notices
Errors (4)
- NSEC3 proving non-existence of www.dibbs.bsm.dla.mil/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of www.dibbs.bsm.dla.mil/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- www.dibbs.bsm.dla.mil/DS has errors; select the "Denial of existence" DNSSEC option to see them.
- www.dibbs.bsm.dla.mil/AAAA has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (20)
- NSEC3 proving non-existence of www.dibbs.bsm.dla.mil/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of www.dibbs.bsm.dla.mil/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- bsm.dla.mil/DS (alg 8, id 526): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bsm.dla.mil/DS (alg 8, id 526): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bsm.dla.mil/DS (alg 8, id 526): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- bsm.dla.mil/DS (alg 8, id 526): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- bsm.dla.mil/DS (alg 8, id 62299): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bsm.dla.mil/DS (alg 8, id 62299): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bsm.dla.mil/DS (alg 8, id 62299): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- bsm.dla.mil/DS (alg 8, id 62299): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- dla.mil/DS (alg 8, id 60304): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- dla.mil/DS (alg 8, id 60304): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- dla.mil/DS (alg 8, id 60304): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- dla.mil/DS (alg 8, id 60304): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- mil/DS (alg 8, id 7765): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- mil/DS (alg 8, id 7765): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- mil/DS (alg 8, id 7765): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- mil/DS (alg 8, id 7765): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- www.dibbs.bsm.dla.mil/SOA: No response was received until the UDP payload size was decreased, indicating that the server might be attempting to send a payload that exceeds the path maximum transmission unit (PMTU) size. See RFC 6891, Sec. 6.2.6. (214.22.172.9, UDP_-_EDNS0_4096_D_K_0x20)
- www.dibbs.bsm.dla.mil/DS has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.