unchat.cat
Updated:
2020-05-05 21:37:05 UTC (2061 days ago)
Go to most recent »
Notices
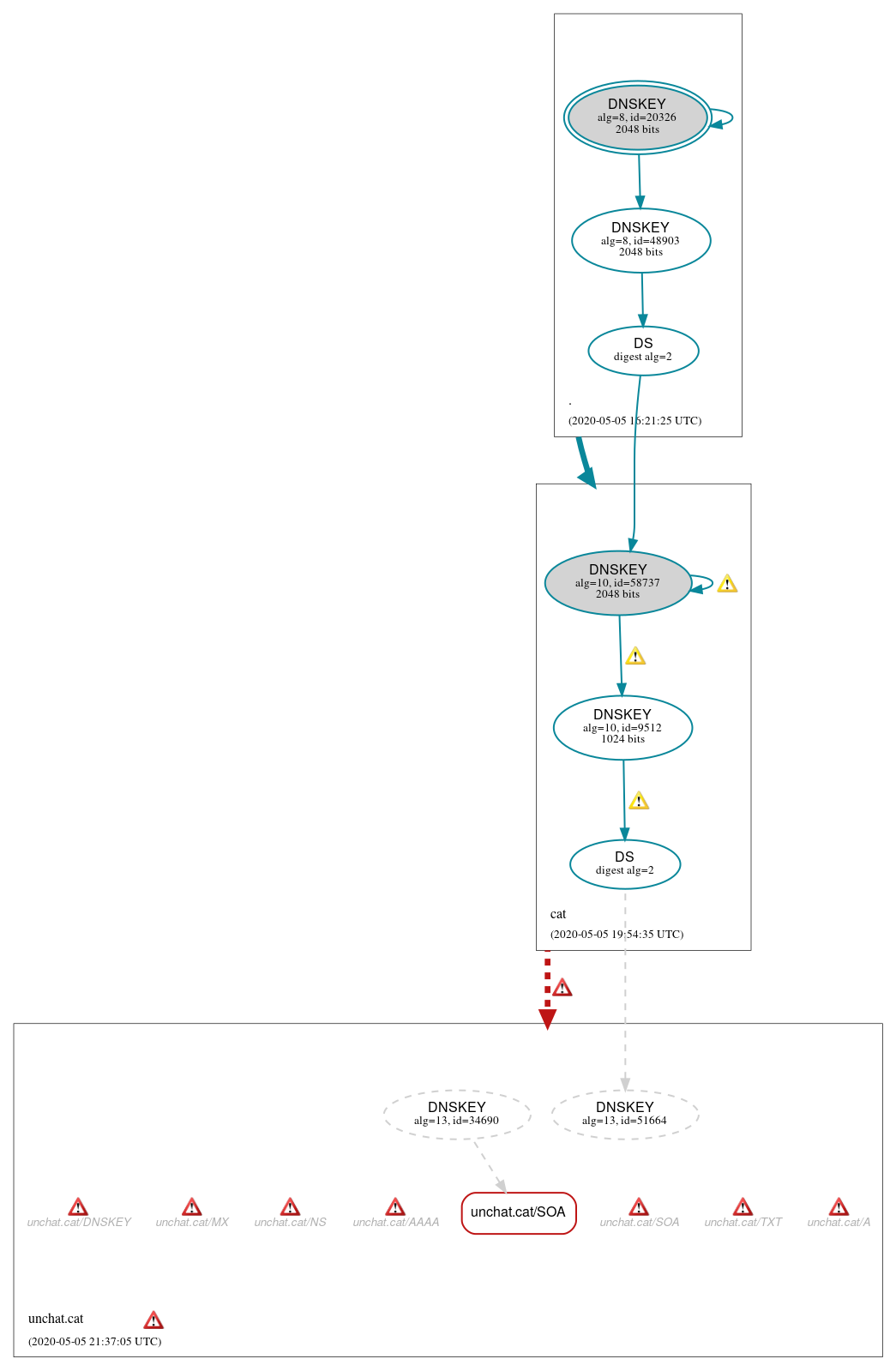
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (1)
- unchat.cat/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (6)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 48903)
- cat/DNSKEY (alg 10, id 58737)
- cat/DNSKEY (alg 10, id 9512)
- cat/DS (alg 10, id 58737)
- unchat.cat/DS (alg 13, id 51664)
Non_existent (2)
- unchat.cat/DNSKEY (alg 13, id 34690)
- unchat.cat/DNSKEY (alg 13, id 51664)
 Delegation status
Delegation status
Bogus (1)
- cat to unchat.cat
Secure (1)
- . to cat
 Notices
Notices
Errors (12)
- cat to unchat.cat: No valid RRSIGs made by a key corresponding to a DS RR were found covering the DNSKEY RRset, resulting in no secure entry point (SEP) into the zone. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11.
- unchat.cat zone: The server(s) responded over UDP with a malformed response or with an invalid RCODE. See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11)
- unchat.cat/A: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K)
- unchat.cat/AAAA: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K)
- unchat.cat/DNSKEY: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K, UDP_-_EDNS0_512_D_K)
- unchat.cat/MX: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K, UDP_-_EDNS0_512_D_K)
- unchat.cat/NS: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K)
- unchat.cat/SOA: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K, UDP_-_EDNS0_4096_D_K_0x20)
- unchat.cat/TXT: The response had an invalid RCODE (23). See RFC 1035, Sec. 4.1.1. (45.150.187.207, 45.150.187.208, 2a0f:de00:ffff::10, 2a0f:de00:ffff::11, UDP_-_EDNS0_4096_D_K)
- unchat.cat/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- noaw6d90fy.unchat.cat/A has errors; select the "Denial of existence" DNSSEC option to see them.
- unchat.cat/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (4)
- RRSIG cat/DNSKEY alg 10, id 58737: DNSSEC implementers are recommended against implementing signing with DNSSEC algorithm 10 (RSASHA512). See RFC 8624, Sec. 3.1.
- RRSIG cat/DNSKEY alg 10, id 58737: DNSSEC implementers are recommended against implementing signing with DNSSEC algorithm 10 (RSASHA512). See RFC 8624, Sec. 3.1.
- RRSIG unchat.cat/DS alg 10, id 9512: DNSSEC implementers are recommended against implementing signing with DNSSEC algorithm 10 (RSASHA512). See RFC 8624, Sec. 3.1.
- unchat.cat/DS has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.