tcp53.ch
Updated:
2022-11-09 13:58:09 UTC (1134 days ago)
Go to most recent »
Notices
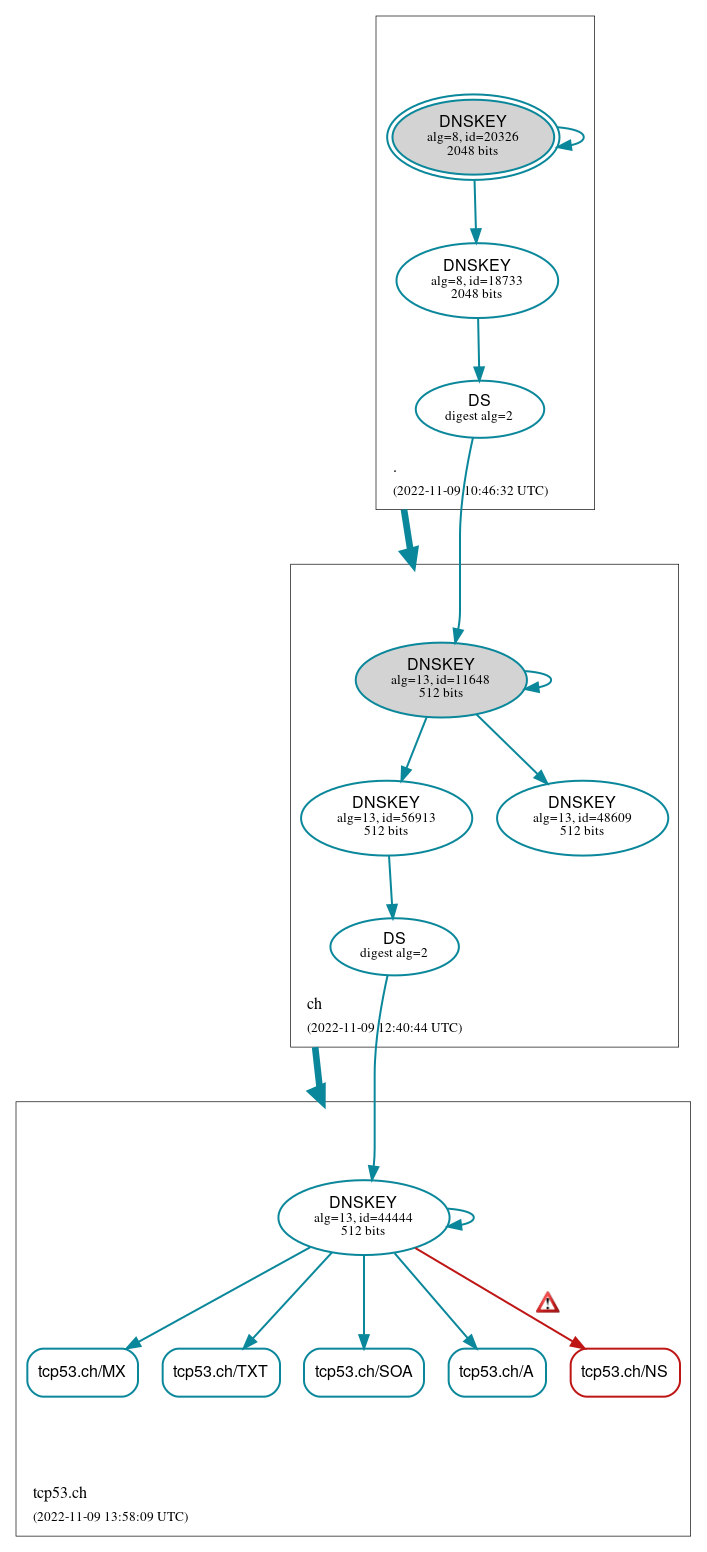
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (1)
- tcp53.ch/NS
Secure (4)
- tcp53.ch/A
- tcp53.ch/MX
- tcp53.ch/SOA
- tcp53.ch/TXT
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (8)
- ./DNSKEY (alg 8, id 18733)
- ./DNSKEY (alg 8, id 20326)
- ch/DNSKEY (alg 13, id 11648)
- ch/DNSKEY (alg 13, id 48609)
- ch/DNSKEY (alg 13, id 56913)
- ch/DS (alg 13, id 11648)
- tcp53.ch/DNSKEY (alg 13, id 44444)
- tcp53.ch/DS (alg 13, id 44444)
 Delegation status
Delegation status
Secure (2)
- . to ch
- ch to tcp53.ch
 Notices
Notices
Errors (1)
- RRSIG tcp53.ch/NS alg 13, id 44444: The cryptographic signature of the RRSIG RR does not properly validate. See RFC 4035, Sec. 5.3.3.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.