kenic.or.ke
Updated:
2021-06-24 07:50:14 UTC (1244 days ago)
Go to most recent »
Notices
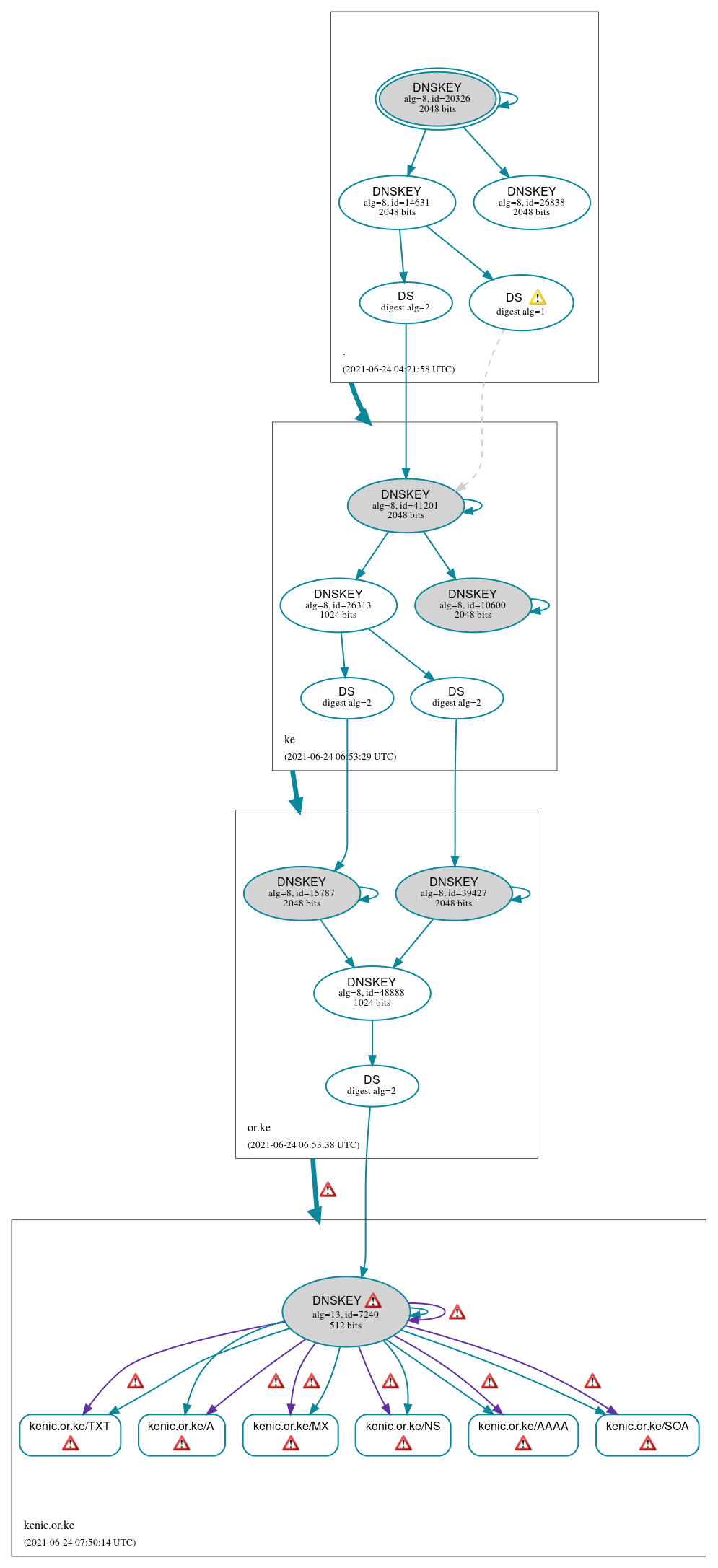
DNSSEC Authentication Chain
 RRset status
RRset status
Secure (6)
- kenic.or.ke/A
- kenic.or.ke/AAAA
- kenic.or.ke/MX
- kenic.or.ke/NS
- kenic.or.ke/SOA
- kenic.or.ke/TXT
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (15)
- ./DNSKEY (alg 8, id 14631)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 26838)
- ke/DNSKEY (alg 8, id 10600)
- ke/DNSKEY (alg 8, id 26313)
- ke/DNSKEY (alg 8, id 41201)
- ke/DS (alg 8, id 41201)
- ke/DS (alg 8, id 41201)
- kenic.or.ke/DNSKEY (alg 13, id 7240)
- kenic.or.ke/DS (alg 13, id 7240)
- or.ke/DNSKEY (alg 8, id 15787)
- or.ke/DNSKEY (alg 8, id 39427)
- or.ke/DNSKEY (alg 8, id 48888)
- or.ke/DS (alg 8, id 15787)
- or.ke/DS (alg 8, id 39427)
 Delegation status
Delegation status
Secure (3)
- . to ke
- ke to or.ke
- or.ke to kenic.or.ke
 Notices
Notices
Errors (19)
- RRSIG kenic.or.ke/A alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG kenic.or.ke/AAAA alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG kenic.or.ke/DNSKEY alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG kenic.or.ke/MX alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG kenic.or.ke/NS alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG kenic.or.ke/SOA alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- RRSIG kenic.or.ke/TXT alg 13, id 7240: The Signature Expiration field of the RRSIG RR (2021-06-24 00:00:00+00:00) is 7 hours, 50 minutes in the past. See RFC 4035, Sec. 5.3.1.
- kenic.or.ke/A: No RRSIG covering the RRset was returned in the response. See RFC 4035, Sec. 3.1.1. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN)
- kenic.or.ke/AAAA: No RRSIG covering the RRset was returned in the response. See RFC 4035, Sec. 3.1.1. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN)
- kenic.or.ke/DNSKEY (alg 13, id 7240): The DNSKEY RR was not found in the DNSKEY RRset returned by one or more servers. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- kenic.or.ke/MX: No RRSIG covering the RRset was returned in the response. See RFC 4035, Sec. 3.1.1. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- kenic.or.ke/NS: No RRSIG covering the RRset was returned in the response. See RFC 4035, Sec. 3.1.1. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN)
- kenic.or.ke/SOA: No RRSIG covering the RRset was returned in the response. See RFC 4035, Sec. 3.1.1. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, TCP_-_EDNS0_4096_D_N, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_4096_D_KN_0x20)
- kenic.or.ke/TXT: No RRSIG covering the RRset was returned in the response. See RFC 4035, Sec. 3.1.1. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN)
- or.ke to kenic.or.ke: No valid RRSIGs made by a key corresponding to a DS RR were found covering the DNSKEY RRset, resulting in no secure entry point (SEP) into the zone. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11. (196.1.4.148, 204.42.254.5, 204.61.216.7, 2001:418:3f4::5, 2001:500:14:6007:ad::1, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- or.ke to kenic.or.ke: The DS RRset for the zone included algorithm 13 (ECDSAP256SHA256), but no DS RR matched a DNSKEY with algorithm 13 that signs the zone's DNSKEY RRset. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11. (196.1.4.148, 2001:43f8:10:0:6818:d6ff:fe71:353e, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- mwz54cdge9.kenic.or.ke/A has errors; select the "Denial of existence" DNSSEC option to see them.
- kenic.or.ke/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- kenic.or.ke/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (5)
- ke/DS (alg 8, id 41201): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- ke/DS (alg 8, id 41201): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- ke/DS (alg 8, id 41201): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- ke/DS (alg 8, id 41201): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- or.ke to kenic.or.ke: Authoritative AAAA records exist for ns.anycast.kenic.or.ke, but there are no corresponding AAAA glue records. See RFC 1034, Sec. 4.2.2.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.