ipfs.io
Updated:
2022-10-16 10:03:09 UTC (618 days ago)
Update now
Notices
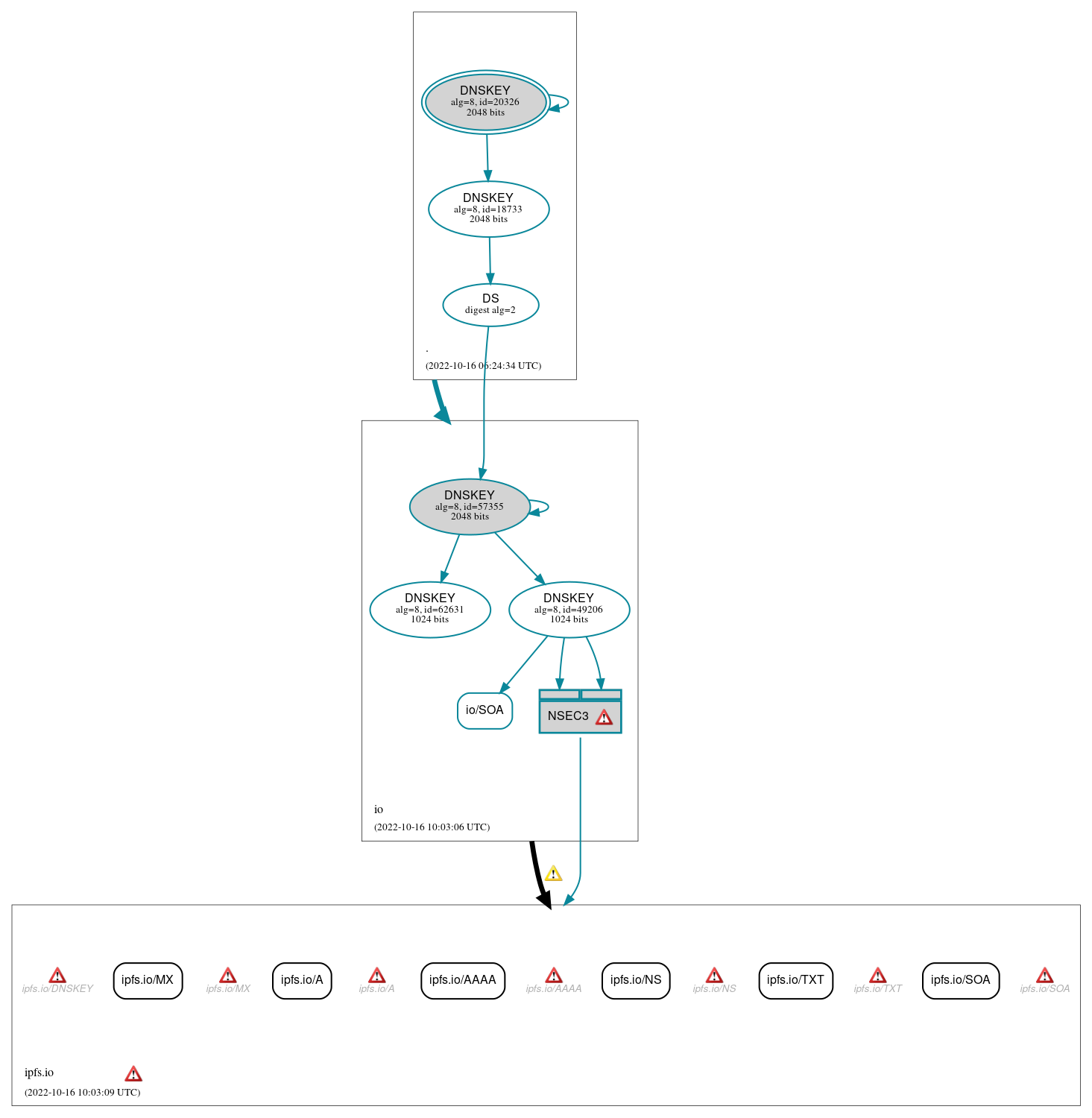
DNSSEC Authentication Chain
 RRset status
RRset status
Insecure (6)
- ipfs.io/A
- ipfs.io/AAAA
- ipfs.io/MX
- ipfs.io/NS
- ipfs.io/SOA
- ipfs.io/TXT
Secure (1)
- io/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (7)
- ./DNSKEY (alg 8, id 18733)
- ./DNSKEY (alg 8, id 20326)
- NSEC3 proving non-existence of ipfs.io/DS
- io/DNSKEY (alg 8, id 49206)
- io/DNSKEY (alg 8, id 57355)
- io/DNSKEY (alg 8, id 62631)
- io/DS (alg 8, id 57355)
 Delegation status
Delegation status
Insecure (1)
- io to ipfs.io
Secure (1)
- . to io
 Notices
Notices
Errors (17)
- NSEC3 proving non-existence of ipfs.io/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ipfs.io/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- ipfs.io zone: The server(s) responded over TCP with a malformed response or with an invalid RCODE. See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1)
- ipfs.io zone: The server(s) responded over UDP with a malformed response or with an invalid RCODE. See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1)
- ipfs.io/A: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN)
- ipfs.io/AAAA: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN)
- ipfs.io/DNSKEY: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- ipfs.io/MX: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- ipfs.io/NS: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN)
- ipfs.io/SOA: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, TCP_-_EDNS0_4096_D_N)
- ipfs.io/SOA: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_4096_D_KN_0x20)
- ipfs.io/TXT: The response had an invalid RCODE (REFUSED). See RFC 1035, Sec. 4.1.1. (208.80.124.13, 208.80.126.13, 208.94.148.13, 2600:1800:5::1, 2600:1801:6::1, 2600:1802:7::1, UDP_-_EDNS0_4096_D_KN)
- ipfs.io/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- ipfs.io/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
- 9kwrao4nlf.ipfs.io/A has errors; select the "Denial of existence" DNSSEC option to see them.
- ipfs.io/DS has errors; select the "Denial of existence" DNSSEC option to see them.
- ipfs.io/NSEC3PARAM has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (4)
- NSEC3 proving non-existence of ipfs.io/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ipfs.io/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- io to ipfs.io: The following NS name(s) were found in the authoritative NS RRset, but not in the delegation NS RRset (i.e., in the io zone): ns5.dnsmadeeasy.com, ns7.dnsmadeeasy.com, ns6.dnsmadeeasy.com See RFC 1034, Sec. 4.2.2.
- ipfs.io/DS has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.