he.net
Updated:
2024-08-06 08:00:00 UTC (562 days ago)
Go to most recent »
Notices
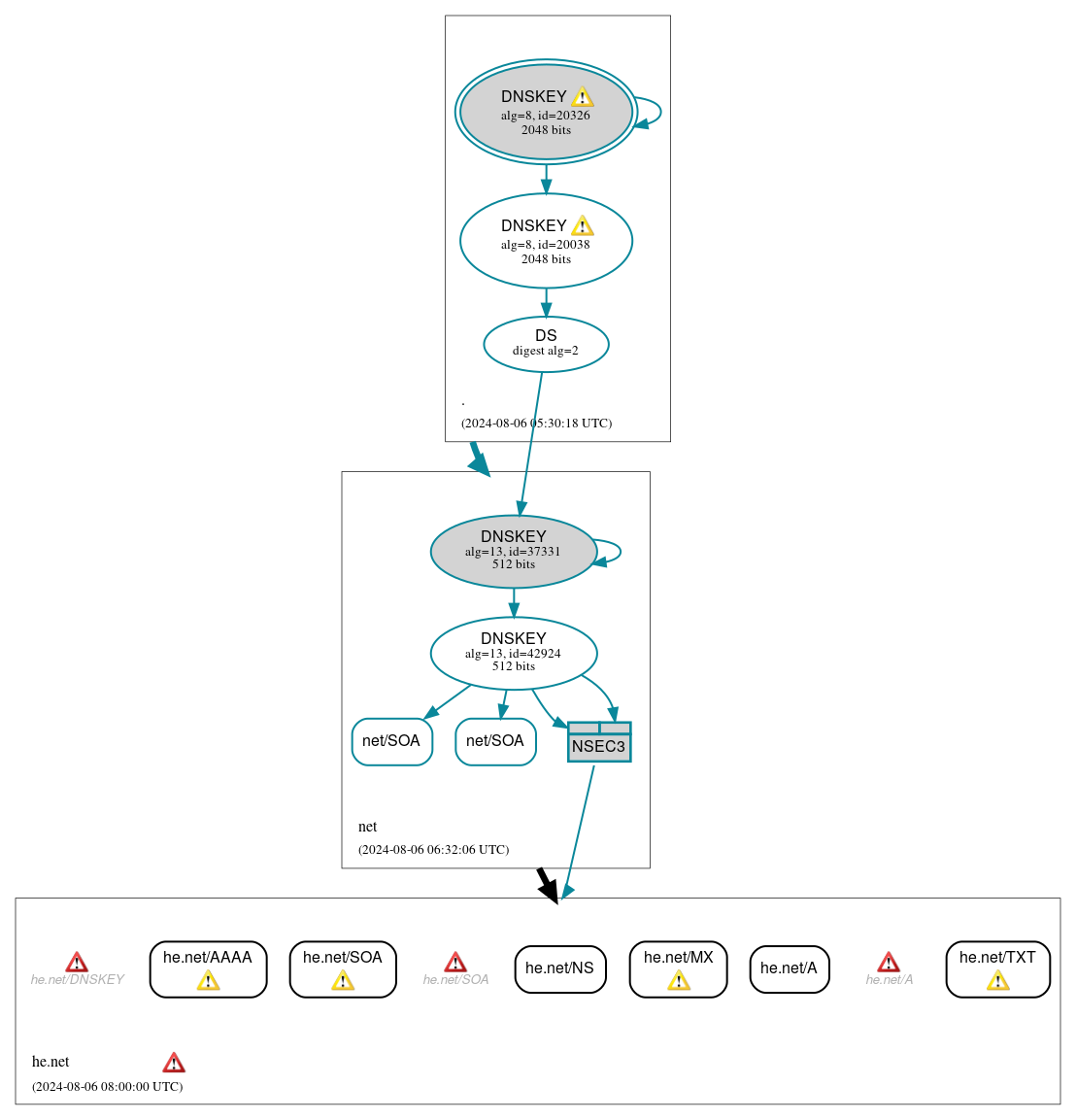
DNSSEC Authentication Chain
 RRset status
RRset status
Insecure (6)
- he.net/A
- he.net/AAAA
- he.net/MX
- he.net/NS
- he.net/SOA
- he.net/TXT
Secure (2)
- net/SOA
- net/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (6)
- ./DNSKEY (alg 8, id 20038)
- ./DNSKEY (alg 8, id 20326)
- NSEC3 proving non-existence of he.net/DS
- net/DNSKEY (alg 13, id 37331)
- net/DNSKEY (alg 13, id 42924)
- net/DS (alg 13, id 37331)
 Delegation status
Delegation status
Insecure (1)
- net to he.net
Secure (1)
- . to net
 Notices
Notices
Errors (7)
- he.net zone: The server(s) responded over TCP with a malformed response or with an invalid RCODE. See RFC 1035, Sec. 4.1.1. (216.66.80.18)
- he.net/A: The UDP connection was refused (ECONNREFUSED). See RFC 1035, Sec. 4.2. (216.66.80.18, UDP_-_EDNS0_4096_D_KN)
- he.net/DNSKEY: The TCP connection was refused (ECONNREFUSED). See RFC 1035, Sec. 4.2. (216.66.80.18, TCP_-_EDNS0_4096_D_KN)
- he.net/SOA: The TCP connection was refused (ECONNREFUSED). See RFC 1035, Sec. 4.2. (216.66.80.18, TCP_-_EDNS0_4096_D_N)
- he.net/SOA: The UDP connection was refused (ECONNREFUSED). See RFC 1035, Sec. 4.2. (216.66.80.18, UDP_-_EDNS0_4096_D_KN)
- fmah6.9trdw.he.net/A has errors; select the "Denial of existence" DNSSEC option to see them.
- he.net/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (7)
- ./DNSKEY (alg 8, id 20038): The server appears to support DNS cookies but did not return a COOKIE option. See RFC 7873, Sec. 5.2.3. (2001:500:2f::f, UDP_-_EDNS0_4096_D_KN)
- ./DNSKEY (alg 8, id 20326): The server appears to support DNS cookies but did not return a COOKIE option. See RFC 7873, Sec. 5.2.3. (2001:500:2f::f, UDP_-_EDNS0_4096_D_KN)
- he.net/AAAA: No response was received until the UDP payload size was decreased, indicating that the server might be attempting to send a payload that exceeds the path maximum transmission unit (PMTU) size. See RFC 6891, Sec. 6.2.6. (216.66.80.18, UDP_-_EDNS0_4096_D_KN)
- he.net/MX: No response was received until the UDP payload size was decreased, indicating that the server might be attempting to send a payload that exceeds the path maximum transmission unit (PMTU) size. See RFC 6891, Sec. 6.2.6. (216.66.80.18, UDP_-_EDNS0_4096_D_KN)
- he.net/SOA: No response was received until the UDP payload size was decreased, indicating that the server might be attempting to send a payload that exceeds the path maximum transmission unit (PMTU) size. See RFC 6891, Sec. 6.2.6. (216.66.80.18, UDP_-_EDNS0_4096_D_KN_0x20)
- he.net/TXT: No response was received until the UDP payload size was decreased, indicating that the server might be attempting to send a payload that exceeds the path maximum transmission unit (PMTU) size. See RFC 6891, Sec. 6.2.6. (216.66.80.18, UDP_-_EDNS0_4096_D_KN)
- he.net/CNAME has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.