gatech.edu
Updated:
2024-04-18 18:54:20 UTC (600 days ago)
Go to most recent »
Notices
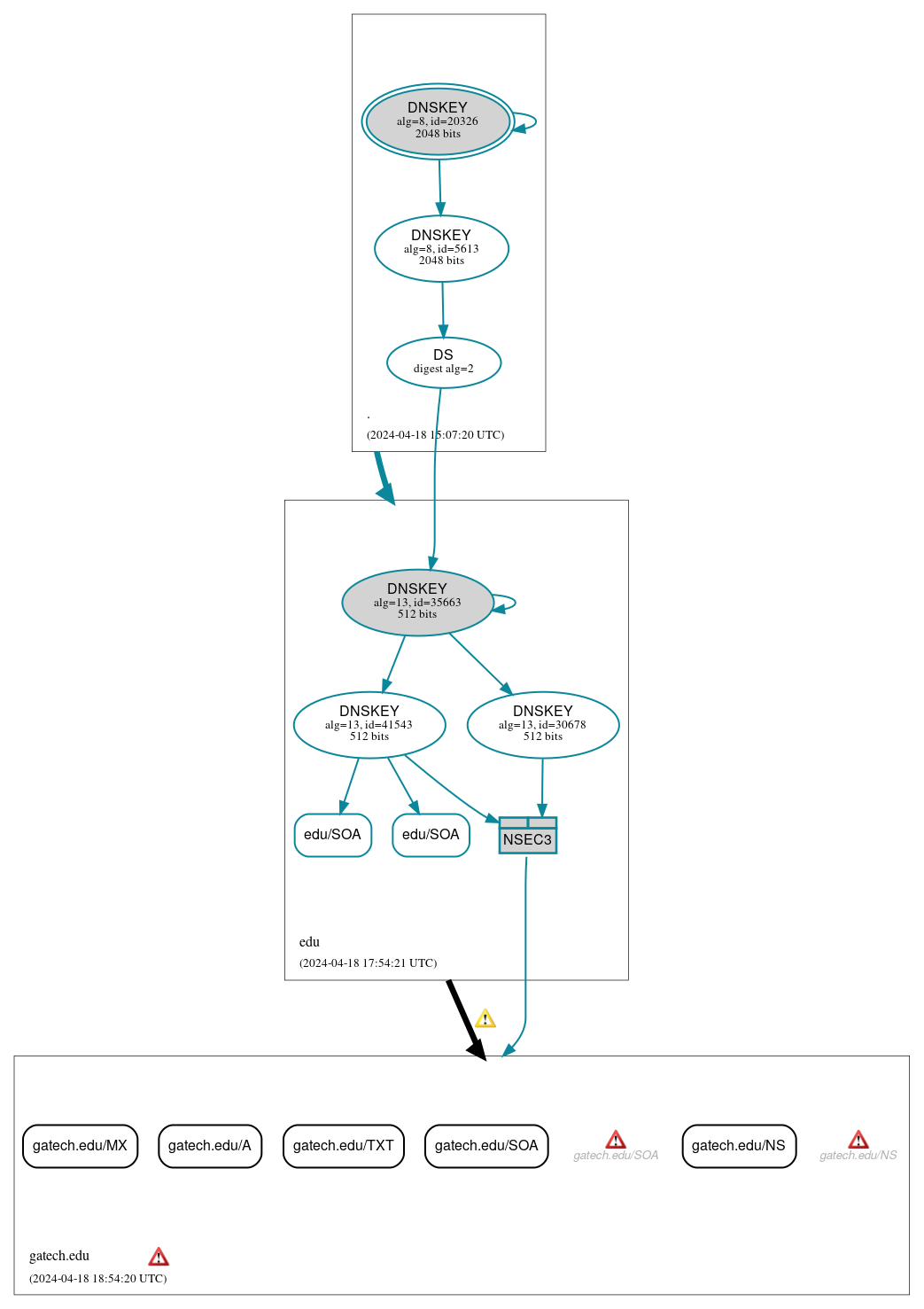
DNSSEC Authentication Chain
 RRset status
RRset status
Insecure (5)
- gatech.edu/A
- gatech.edu/MX
- gatech.edu/NS
- gatech.edu/SOA
- gatech.edu/TXT
Secure (2)
- edu/SOA
- edu/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (7)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 5613)
- NSEC3 proving non-existence of gatech.edu/DS
- edu/DNSKEY (alg 13, id 30678)
- edu/DNSKEY (alg 13, id 35663)
- edu/DNSKEY (alg 13, id 41543)
- edu/DS (alg 13, id 35663)
 Delegation status
Delegation status
Insecure (1)
- edu to gatech.edu
Secure (1)
- . to edu
 Notices
Notices
Errors (3)
- gatech.edu zone: The server(s) were not responsive to queries over TCP. See RFC 1035, Sec. 4.2. (3.227.90.38)
- gatech.edu/NS: The response (161 bytes) was malformed. (168.24.2.35, UDP_-_NOEDNS_)
- gatech.edu/SOA: No response was received from the server over TCP (tried 3 times). See RFC 1035, Sec. 4.2. (3.227.90.38, TCP_-_EDNS0_4096_D_N)
Warnings (1)
- edu to gatech.edu: Authoritative AAAA records exist for dns1.gatech.edu, but there are no corresponding AAAA glue records. See RFC 1034, Sec. 4.2.2.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.