falcon.example.pq-dnssec.dedyn.io
Updated:
2022-03-31 09:50:53 UTC (1359 days ago)
Go to most recent »
Notices
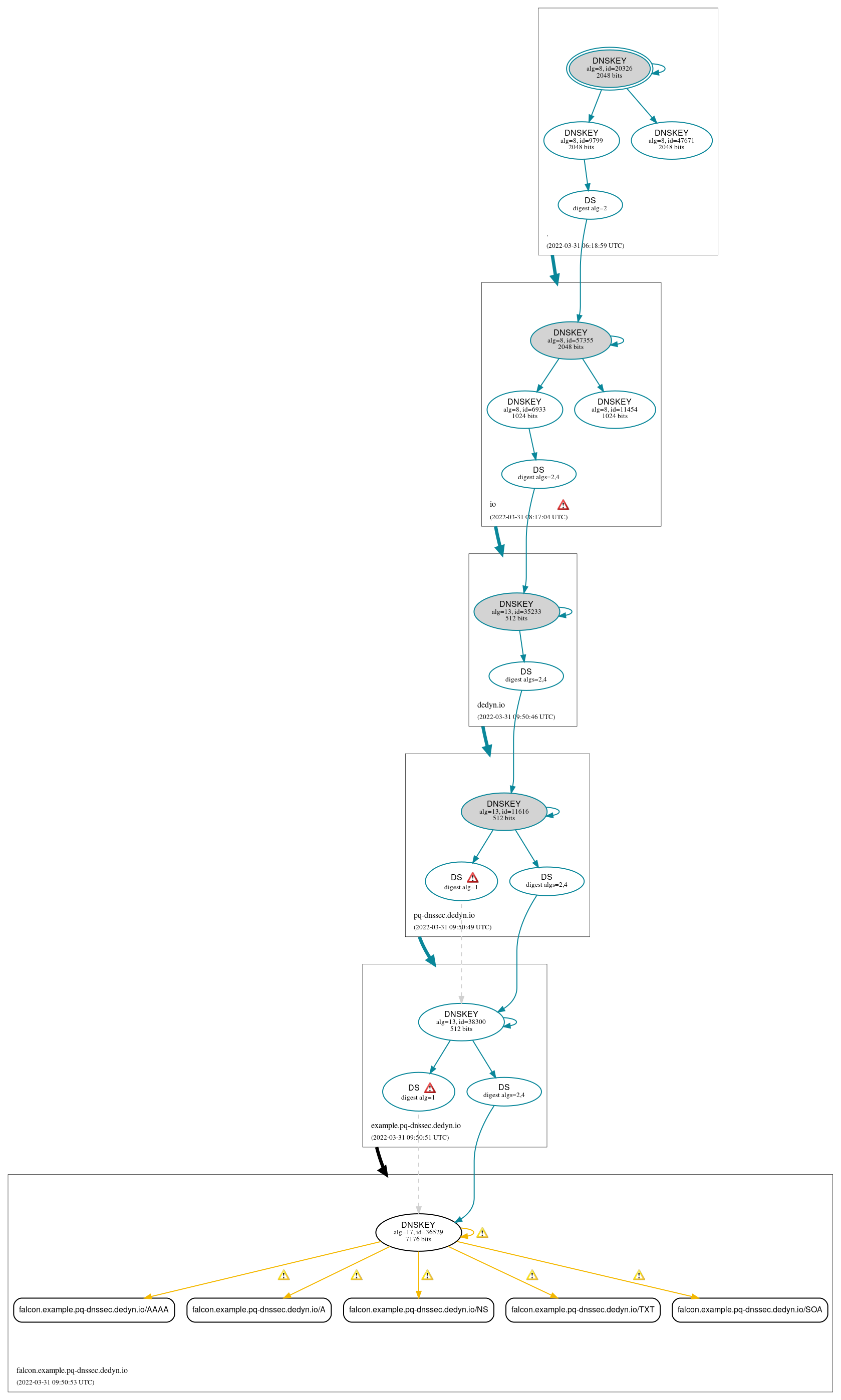
DNSSEC Authentication Chain
 RRset status
RRset status
Insecure (5)
- falcon.example.pq-dnssec.dedyn.io/A
- falcon.example.pq-dnssec.dedyn.io/AAAA
- falcon.example.pq-dnssec.dedyn.io/NS
- falcon.example.pq-dnssec.dedyn.io/SOA
- falcon.example.pq-dnssec.dedyn.io/TXT
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Insecure (1)
- falcon.example.pq-dnssec.dedyn.io/DNSKEY (alg 17, id 36529)
Secure (16)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 47671)
- ./DNSKEY (alg 8, id 9799)
- dedyn.io/DNSKEY (alg 13, id 35233)
- dedyn.io/DS (alg 13, id 35233)
- example.pq-dnssec.dedyn.io/DNSKEY (alg 13, id 38300)
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300)
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300)
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529)
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529)
- io/DNSKEY (alg 8, id 11454)
- io/DNSKEY (alg 8, id 57355)
- io/DNSKEY (alg 8, id 6933)
- io/DS (alg 8, id 57355)
- pq-dnssec.dedyn.io/DNSKEY (alg 13, id 11616)
- pq-dnssec.dedyn.io/DS (alg 13, id 11616)
 Delegation status
Delegation status
Insecure (1)
- example.pq-dnssec.dedyn.io to falcon.example.pq-dnssec.dedyn.io
Secure (4)
- . to io
- dedyn.io to pq-dnssec.dedyn.io
- io to dedyn.io
- pq-dnssec.dedyn.io to example.pq-dnssec.dedyn.io
 Notices
Notices
Errors (1)
- io zone: The server(s) were not responsive to queries over UDP. See RFC 1035, Sec. 4.2. (2a01:8840:9f::17)
Warnings (23)
- RRSIG falcon.example.pq-dnssec.dedyn.io/A alg 17, id 36529: Validation of DNSSEC algorithm 17 (17) is not supported by this code, so the cryptographic status of this RRSIG is unknown. See RFC 4035, Sec. 5.2.
- RRSIG falcon.example.pq-dnssec.dedyn.io/AAAA alg 17, id 36529: Validation of DNSSEC algorithm 17 (17) is not supported by this code, so the cryptographic status of this RRSIG is unknown. See RFC 4035, Sec. 5.2.
- RRSIG falcon.example.pq-dnssec.dedyn.io/DNSKEY alg 17, id 36529: Validation of DNSSEC algorithm 17 (17) is not supported by this code, so the cryptographic status of this RRSIG is unknown. See RFC 4035, Sec. 5.2.
- RRSIG falcon.example.pq-dnssec.dedyn.io/NS alg 17, id 36529: Validation of DNSSEC algorithm 17 (17) is not supported by this code, so the cryptographic status of this RRSIG is unknown. See RFC 4035, Sec. 5.2.
- RRSIG falcon.example.pq-dnssec.dedyn.io/SOA alg 17, id 36529: Validation of DNSSEC algorithm 17 (17) is not supported by this code, so the cryptographic status of this RRSIG is unknown. See RFC 4035, Sec. 5.2.
- RRSIG falcon.example.pq-dnssec.dedyn.io/TXT alg 17, id 36529: Validation of DNSSEC algorithm 17 (17) is not supported by this code, so the cryptographic status of this RRSIG is unknown. See RFC 4035, Sec. 5.2.
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300): In the spirit of RFC 4509, DS records with digest type 1 (SHA-1) might be ignored when DS records with digest type 4 (SHA-384) exist in the same RRset. See RFC 4509, Sec. 3.
- example.pq-dnssec.dedyn.io/DS (alg 13, id 38300): In the spirit of RFC 4509, DS records with digest type 1 (SHA-1) might be ignored when DS records with digest type 4 (SHA-384) exist in the same RRset. See RFC 4509, Sec. 3.
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529): In the spirit of RFC 4509, DS records with digest type 1 (SHA-1) might be ignored when DS records with digest type 4 (SHA-384) exist in the same RRset. See RFC 4509, Sec. 3.
- falcon.example.pq-dnssec.dedyn.io/DS (alg 17, id 36529): In the spirit of RFC 4509, DS records with digest type 1 (SHA-1) might be ignored when DS records with digest type 4 (SHA-384) exist in the same RRset. See RFC 4509, Sec. 3.
- falcon.example.pq-dnssec.dedyn.io/NSEC3PARAM has warnings; select the "Denial of existence" DNSSEC option to see them.
- falcon.example.pq-dnssec.dedyn.io/MX has warnings; select the "Denial of existence" DNSSEC option to see them.
- falcon.example.pq-dnssec.dedyn.io/DNSKEY has warnings; select the "Denial of existence" DNSSEC option to see them.
- falcon.example.pq-dnssec.dedyn.io/CNAME has warnings; select the "Denial of existence" DNSSEC option to see them.
- if2b8xvknt.falcon.example.pq-dnssec.dedyn.io/A has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.