dnssec-test.balug.org
Updated:
2024-09-26 22:10:33 UTC (103 days ago)
Go to most recent »
Notices
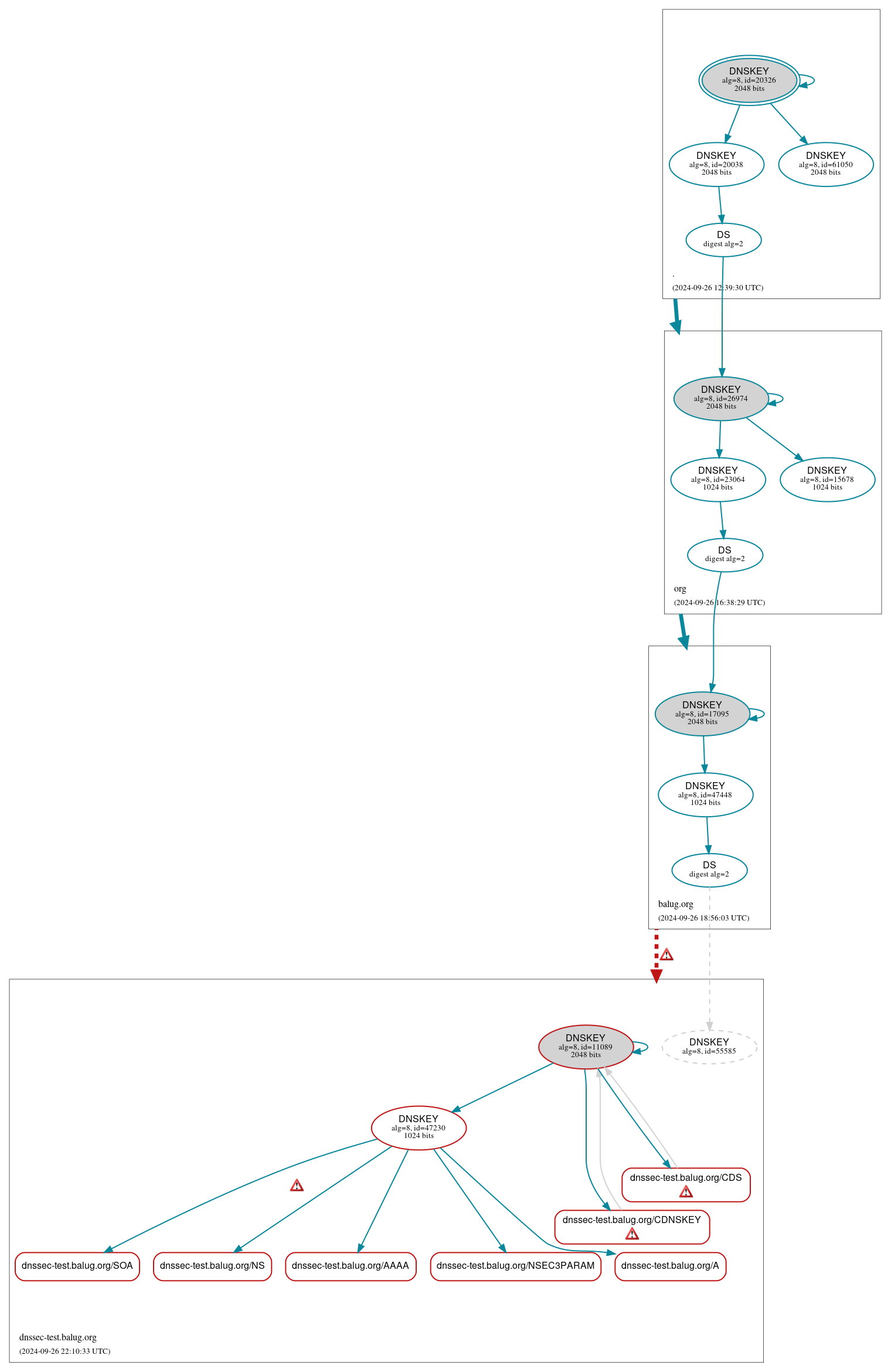
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (7)
- dnssec-test.balug.org/A
- dnssec-test.balug.org/AAAA
- dnssec-test.balug.org/CDNSKEY
- dnssec-test.balug.org/CDS
- dnssec-test.balug.org/NS
- dnssec-test.balug.org/NSEC3PARAM
- dnssec-test.balug.org/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Bogus (2)
- dnssec-test.balug.org/DNSKEY (alg 8, id 11089)
- dnssec-test.balug.org/DNSKEY (alg 8, id 47230)
Secure (11)
- ./DNSKEY (alg 8, id 20038)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 61050)
- balug.org/DNSKEY (alg 8, id 17095)
- balug.org/DNSKEY (alg 8, id 47448)
- balug.org/DS (alg 8, id 17095)
- dnssec-test.balug.org/DS (alg 8, id 55585)
- org/DNSKEY (alg 8, id 15678)
- org/DNSKEY (alg 8, id 23064)
- org/DNSKEY (alg 8, id 26974)
- org/DS (alg 8, id 26974)
Non_existent (1)
- dnssec-test.balug.org/DNSKEY (alg 8, id 55585)
 Delegation status
Delegation status
Bogus (1)
- balug.org to dnssec-test.balug.org
Secure (2)
- . to org
- org to balug.org
 Notices
Notices
Errors (5)
- RRSIG dnssec-test.balug.org/SOA alg 8, id 47230: With a TTL of 3600 the RRSIG RR can be in the cache of a non-validating resolver until 54 minutes after it expires at 2024-09-26 22:16:00+00:00. See RFC 4035, Sec. 5.3.3.
- balug.org to dnssec-test.balug.org: No valid RRSIGs made by a key corresponding to a DS RR were found covering the DNSKEY RRset, resulting in no secure entry point (SEP) into the zone. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11. (96.86.170.229, 2001:470:1f05:19e::2, UDP_-_EDNS0_4096_D_KN)
- balug.org to dnssec-test.balug.org: The DS RRset for the zone included algorithm 8 (RSASHA256), but no DS RR matched a DNSKEY with algorithm 8 that signs the zone's DNSKEY RRset. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11. (96.86.170.229, 2001:470:1f05:19e::2, UDP_-_EDNS0_4096_D_KN)
- dnssec-test.balug.org/CDNSKEY: The CDNSKEY RRset must be signed with a key that is represented in both the current DNSKEY and the current DS RRset. See RFC 7344, Sec. 4.1.
- dnssec-test.balug.org/CDS: The CDS RRset must be signed with a key that is represented in both the current DNSKEY and the current DS RRset. See RFC 7344, Sec. 4.1.
Warnings (2)
- dnssec-test.balug.org/CDNSKEY: The contents of the DS RRset are inconsistent with those of the CDNSKEY RRset. See RFC 7344, Sec. 3, RFC 7344, Sec. 5.
- dnssec-test.balug.org/CDS: The contents of the DS RRset are inconsistent with those of the CDS RRset. See RFC 7344, Sec. 3, RFC 7344, Sec. 5.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.