ac.bw
Updated:
2021-02-02 13:05:27 UTC (1794 days ago)
Go to most recent »
Notices
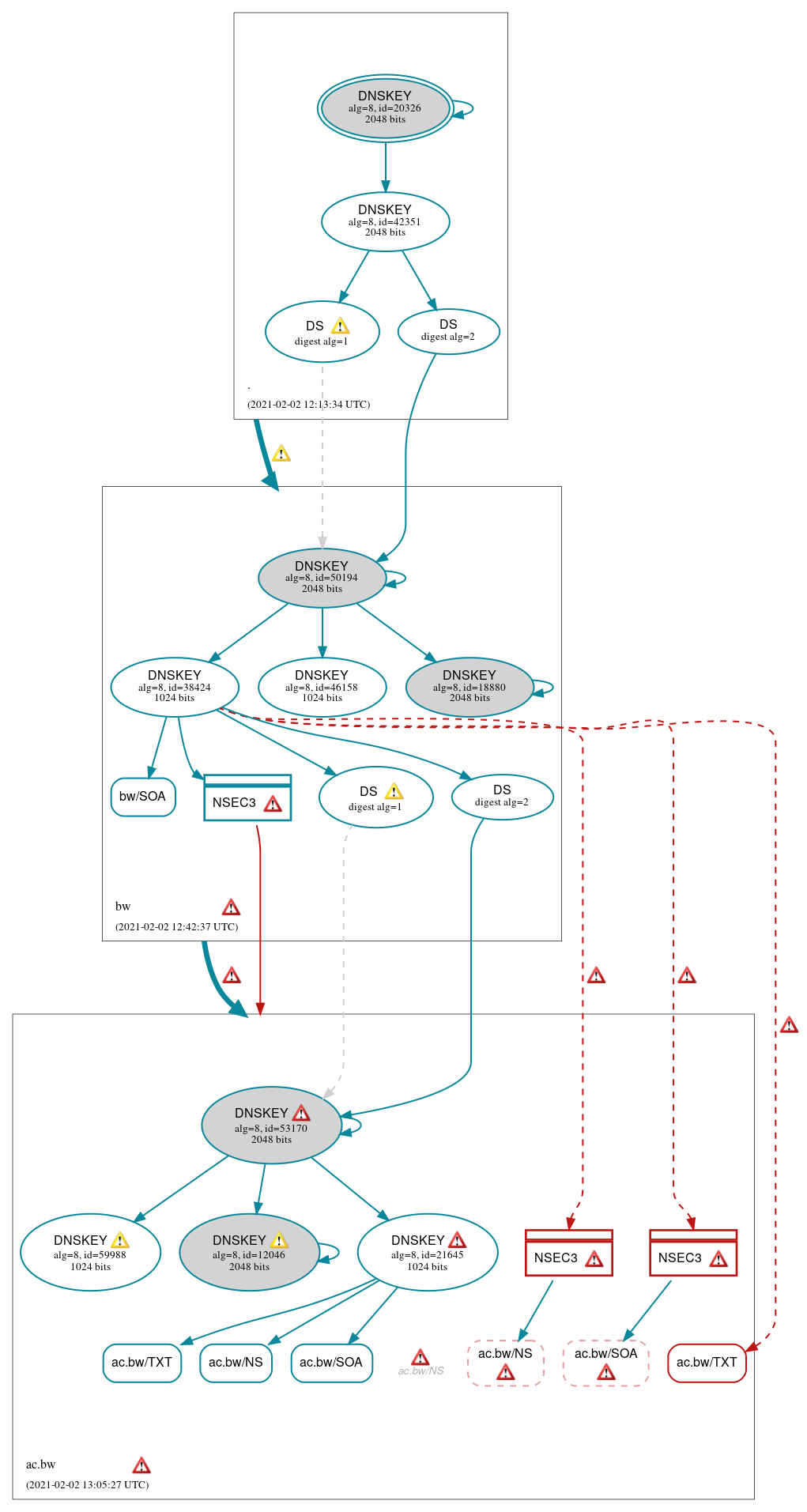
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (3)
- ac.bw/NS (NODATA)
- ac.bw/SOA (NODATA)
- ac.bw/TXT
Secure (4)
- ac.bw/NS
- ac.bw/SOA
- ac.bw/TXT
- bw/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Bogus (2)
- NSEC3 proving non-existence of ac.bw/NS
- NSEC3 proving non-existence of ac.bw/SOA
Secure (15)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 42351)
- NSEC3 proving non-existence of ac.bw/DS
- ac.bw/DNSKEY (alg 8, id 12046)
- ac.bw/DNSKEY (alg 8, id 21645)
- ac.bw/DNSKEY (alg 8, id 53170)
- ac.bw/DNSKEY (alg 8, id 59988)
- ac.bw/DS (alg 8, id 53170)
- ac.bw/DS (alg 8, id 53170)
- bw/DNSKEY (alg 8, id 18880)
- bw/DNSKEY (alg 8, id 38424)
- bw/DNSKEY (alg 8, id 46158)
- bw/DNSKEY (alg 8, id 50194)
- bw/DS (alg 8, id 50194)
- bw/DS (alg 8, id 50194)
 Delegation status
Delegation status
Secure (2)
- . to bw
- bw to ac.bw
 Notices
Notices
Errors (32)
- NSEC3 proving non-existence of ac.bw/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/DS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/DS: The NS bit was not set in the bitmap of the NSEC3 RR corresponding to the delegated name (ac.bw). See RFC 5155, Sec. 8.9.
- NSEC3 proving non-existence of ac.bw/DS: The NS bit was not set in the bitmap of the NSEC3 RR corresponding to the delegated name (ac.bw). See RFC 5155, Sec. 8.9.
- NSEC3 proving non-existence of ac.bw/NS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/NS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/NS: The following queries resulted in an answer response, even though the bitmap in the NSEC3 RR indicates that the queried records don't exist: ac.bw/SOA, ac.bw/NS, ac.bw/DNSKEY See RFC 5155, Sec. 8.5.
- NSEC3 proving non-existence of ac.bw/NS: The following queries resulted in an answer response, even though the bitmap in the NSEC3 RR indicates that the queried records don't exist: ac.bw/SOA, ac.bw/NS, ac.bw/DNSKEY See RFC 5155, Sec. 8.5.
- NSEC3 proving non-existence of ac.bw/SOA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/SOA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/SOA: The following queries resulted in an answer response, even though the bitmap in the NSEC3 RR indicates that the queried records don't exist: ac.bw/SOA, ac.bw/NS, ac.bw/DNSKEY See RFC 5155, Sec. 8.5.
- NSEC3 proving non-existence of ac.bw/SOA: The following queries resulted in an answer response, even though the bitmap in the NSEC3 RR indicates that the queried records don't exist: ac.bw/SOA, ac.bw/NS, ac.bw/DNSKEY See RFC 5155, Sec. 8.5.
- RRSIG NSEC3 proving non-existence of ac.bw/NS alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (ac.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG NSEC3 proving non-existence of ac.bw/SOA alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (ac.bw). See RFC 4035, Sec. 5.3.1.
- RRSIG ac.bw/TXT alg 8, id 38424: The Signer's Name field of the RRSIG RR (bw) does not match the name of the zone containing the RRset (ac.bw). See RFC 4035, Sec. 5.3.1.
- ac.bw zone: The server(s) did not respond authoritatively for the namespace. See RFC 1035, Sec. 4.1.1. (204.61.216.70, 2001:500:14:6070:ad::1, 2001:43f8:120::72)
- ac.bw zone: The server(s) were not responsive to queries over UDP. See RFC 1035, Sec. 4.2. (2c0f:ff00:0:6::3, 2c0f:ff00:0:6::5, 2c0f:ff00:1:3::226, 2c0f:ff00:1:5::218)
- ac.bw/DNSKEY (alg 8, id 21645): The DNSKEY RR was not found in the DNSKEY RRset returned by one or more servers. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- ac.bw/DNSKEY (alg 8, id 53170): The DNSKEY RR was not found in the DNSKEY RRset returned by one or more servers. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- ac.bw/NS (NODATA): An SOA RR with owner name (bw) not matching the zone name (ac.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN)
- ac.bw/NS: No response was received from the server over UDP (tried 12 times). See RFC 1035, Sec. 4.2. (2c0f:ff00:0:6::3, 2c0f:ff00:0:6::5, 2c0f:ff00:1:3::226, 2c0f:ff00:1:5::218, UDP_-_NOEDNS_)
- ac.bw/SOA (NODATA): An SOA RR with owner name (bw) not matching the zone name (ac.bw) was returned with the NODATA response. See RFC 1034, Sec. 4.3.4, RFC 2308, Sec. 2.2. (168.167.98.226, 196.216.168.72, TCP_-_EDNS0_4096_D_N, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_4096_D_KN_0x20)
- bw to ac.bw: No valid RRSIGs made by a key corresponding to a DS RR were found covering the DNSKEY RRset, resulting in no secure entry point (SEP) into the zone. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- bw to ac.bw: The DS RRset for the zone included algorithm 8 (RSASHA256), but no DS RR matched a DNSKEY with algorithm 8 that signs the zone's DNSKEY RRset. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- bw zone: The server(s) were not responsive to queries over UDP. See RFC 1035, Sec. 4.2. (2c0f:ff00:0:6::3, 2c0f:ff00:0:6::5, 2c0f:ff00:1:3::226)
- ac.bw/MX has errors; select the "Denial of existence" DNSSEC option to see them.
- n4ly5zgiah.ac.bw/A has errors; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/A has errors; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/AAAA has errors; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/DS has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (25)
- . to bw: The following NS name(s) were found in the authoritative NS RRset, but not in the delegation NS RRset (i.e., in the . zone): master.btc.net.bw See RFC 1034, Sec. 4.2.2.
- NSEC3 proving non-existence of ac.bw/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/DS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/NS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/NS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/SOA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of ac.bw/SOA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- ac.bw/DNSKEY (alg 8, id 12046): The DNSKEY RR was not found in the DNSKEY RRset returned by one or more servers. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- ac.bw/DNSKEY (alg 8, id 59988): The DNSKEY RR was not found in the DNSKEY RRset returned by one or more servers. (168.167.98.226, 196.216.168.72, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_512_D_KN)
- ac.bw/DS (alg 8, id 53170): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- ac.bw/DS (alg 8, id 53170): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- ac.bw/DS (alg 8, id 53170): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- ac.bw/DS (alg 8, id 53170): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- bw to ac.bw: The following NS name(s) were found in the authoritative NS RRset, but not in the delegation NS RRset (i.e., in the bw zone): dns1.nic.net.bw, dns2.nic.net.bw, master.btc.net.bw See RFC 1034, Sec. 4.2.2.
- bw/DS (alg 8, id 50194): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bw/DS (alg 8, id 50194): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- bw/DS (alg 8, id 50194): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- bw/DS (alg 8, id 50194): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- ac.bw/MX has warnings; select the "Denial of existence" DNSSEC option to see them.
- n4ly5zgiah.ac.bw/A has warnings; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/A has warnings; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/AAAA has warnings; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/CNAME has warnings; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/DNSKEY has warnings; select the "Denial of existence" DNSSEC option to see them.
- ac.bw/DS has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.