zapaname.us
Updated:
2024-10-19 05:59:49 UTC (34 days ago)
Update now
Notices
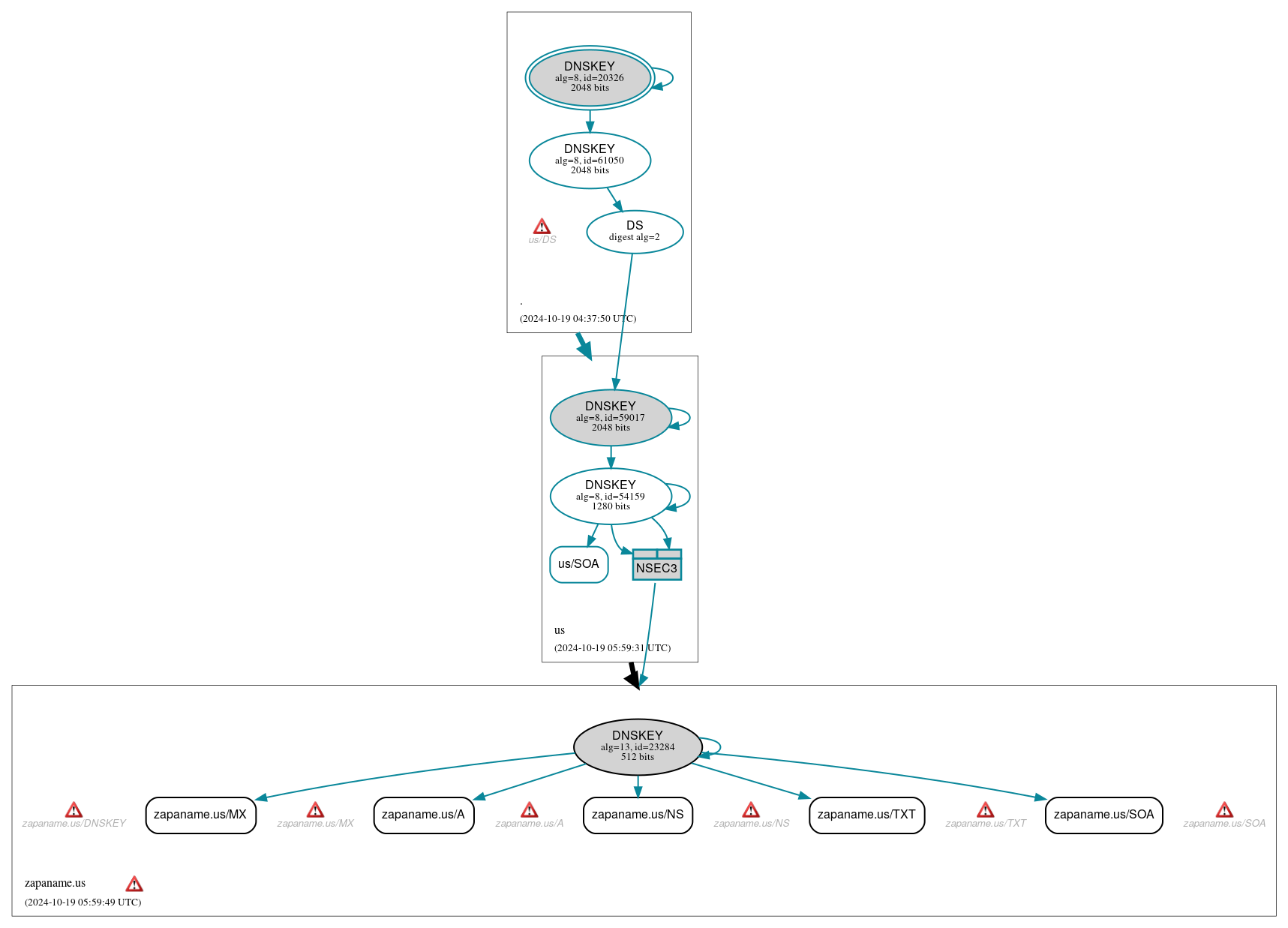
DNSSEC Authentication Chain
 RRset status
RRset status
Insecure (5)
- zapaname.us/A
- zapaname.us/MX
- zapaname.us/NS
- zapaname.us/SOA
- zapaname.us/TXT
Secure (1)
- us/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Insecure (1)
- zapaname.us/DNSKEY (alg 13, id 23284)
Secure (6)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 61050)
- NSEC3 proving non-existence of zapaname.us/DS
- us/DNSKEY (alg 8, id 54159)
- us/DNSKEY (alg 8, id 59017)
- us/DS (alg 8, id 59017)
 Delegation status
Delegation status
Insecure (1)
- us to zapaname.us
Secure (1)
- . to us
 Notices
Notices
Errors (17)
- us/DS: No response was received from the server over UDP (tried 9 times). See RFC 1035, Sec. 4.2. (192.33.4.12, UDP_-_EDNS0_4096_D)
- zapaname.us zone: The server(s) responded over TCP with a malformed response or with an invalid RCODE. See RFC 1035, Sec. 4.1.1. (35.208.110.23)
- zapaname.us zone: The server(s) responded over UDP with a malformed response or with an invalid RCODE. See RFC 1035, Sec. 4.1.1. (35.208.110.23)
- zapaname.us/A: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, UDP_-_NOEDNS_)
- zapaname.us/DNSKEY: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, UDP_-_EDNS0_512_D_KN, UDP_-_NOEDNS_)
- zapaname.us/MX: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, UDP_-_EDNS0_512_D_KN, UDP_-_NOEDNS_)
- zapaname.us/NS: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, UDP_-_NOEDNS_)
- zapaname.us/SOA: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, TCP_-_NOEDNS_)
- zapaname.us/SOA: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, UDP_-_NOEDNS_, UDP_-_NOEDNS__0x20)
- zapaname.us/TXT: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (35.208.110.23, UDP_-_NOEDNS_)
- 8h67n.wexyv.zapaname.us/A has errors; select the "Denial of existence" DNSSEC option to see them.
- zapaname.us/CDS has errors; select the "Denial of existence" DNSSEC option to see them.
- zapaname.us/CDNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- zapaname.us/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
- zapaname.us/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- zapaname.us/AAAA has errors; select the "Denial of existence" DNSSEC option to see them.
- zapaname.us/NSEC3PARAM has errors; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.