permanent.access.gpo.gov
Updated:
2025-03-18 13:47:12 UTC (about a month ago)
Update now
Notices
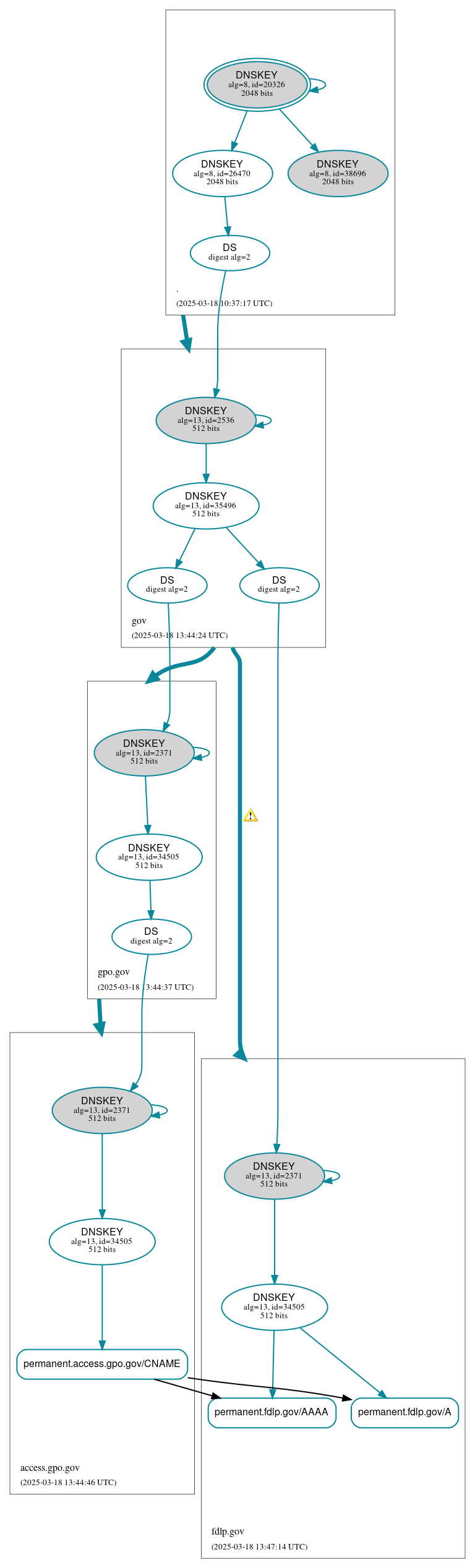
DNSSEC Authentication Chain
 RRset status
RRset status
Secure (3)
- permanent.access.gpo.gov/CNAME
- permanent.fdlp.gov/A
- permanent.fdlp.gov/AAAA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (15)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 26470)
- ./DNSKEY (alg 8, id 38696)
- access.gpo.gov/DNSKEY (alg 13, id 2371)
- access.gpo.gov/DNSKEY (alg 13, id 34505)
- access.gpo.gov/DS (alg 13, id 2371)
- fdlp.gov/DNSKEY (alg 13, id 2371)
- fdlp.gov/DNSKEY (alg 13, id 34505)
- fdlp.gov/DS (alg 13, id 2371)
- gov/DNSKEY (alg 13, id 2536)
- gov/DNSKEY (alg 13, id 35496)
- gov/DS (alg 13, id 2536)
- gpo.gov/DNSKEY (alg 13, id 2371)
- gpo.gov/DNSKEY (alg 13, id 34505)
- gpo.gov/DS (alg 13, id 2371)
 Delegation status
Delegation status
Secure (4)
- . to gov
- gov to fdlp.gov
- gov to gpo.gov
- gpo.gov to access.gpo.gov
 Notices
Notices
Warnings (2)
- gov to fdlp.gov: The following NS name(s) were found in the authoritative NS RRset, but not in the delegation NS RRset (i.e., in the gov zone): ns1.fdlp.gov, ns2.fdlp.gov See RFC 1034, Sec. 4.2.2.
- gov to fdlp.gov: The following NS name(s) were found in the delegation NS RRset (i.e., in the gov zone), but not in the authoritative NS RRset: chip.ns.cloudflare.com, cruz.ns.cloudflare.com See RFC 1034, Sec. 4.2.2.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.