nicbr.mil
Updated:
2021-08-26 19:53:41 UTC (1212 days ago)
Update now
Notices
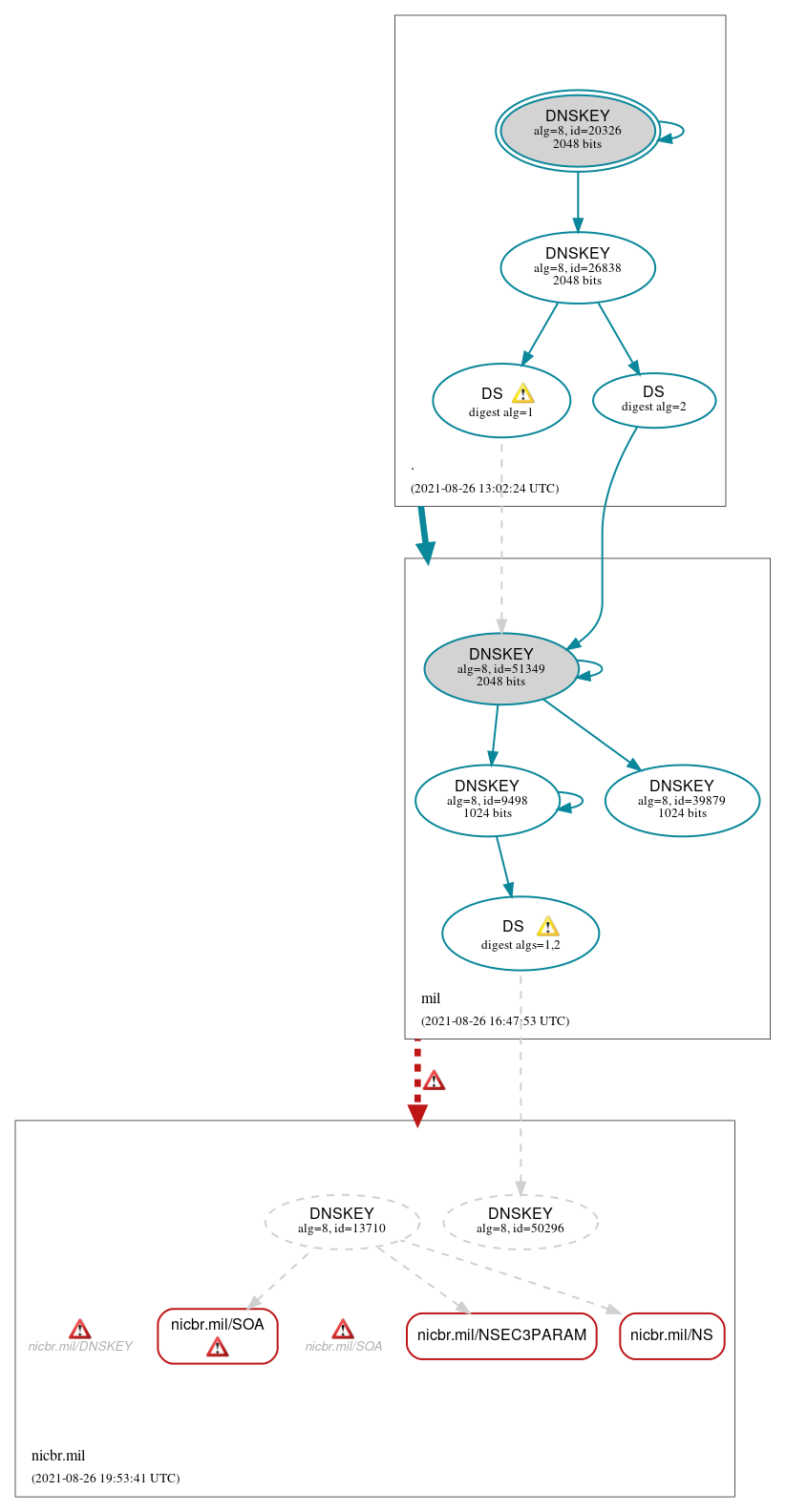
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (3)
- nicbr.mil/NS
- nicbr.mil/NSEC3PARAM
- nicbr.mil/SOA
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (8)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 26838)
- mil/DNSKEY (alg 8, id 39879)
- mil/DNSKEY (alg 8, id 51349)
- mil/DNSKEY (alg 8, id 9498)
- mil/DS (alg 8, id 51349)
- mil/DS (alg 8, id 51349)
- nicbr.mil/DS (alg 8, id 50296)
Non_existent (2)
- nicbr.mil/DNSKEY (alg 8, id 13710)
- nicbr.mil/DNSKEY (alg 8, id 50296)
 Delegation status
Delegation status
Bogus (1)
- mil to nicbr.mil
Secure (1)
- . to mil
 Notices
Notices
Errors (14)
- mil to nicbr.mil: No valid RRSIGs made by a key corresponding to a DS RR were found covering the DNSKEY RRset, resulting in no secure entry point (SEP) into the zone. See RFC 4035, Sec. 2.2, RFC 6840, Sec. 5.11.
- nicbr.mil/DNSKEY: No response was received from the server over UDP (tried 12 times). See RFC 1035, Sec. 4.2. (140.153.43.44, 192.82.113.7, UDP_-_EDNS0_4096_D_KN)
- nicbr.mil/DNSKEY: The response had an invalid RCODE (SERVFAIL). See RFC 1035, Sec. 4.1.1. (130.114.200.6, TCP_-_NOEDNS_)
- nicbr.mil/SOA: DNSSEC was effectively downgraded because the response had an invalid RCODE (SERVFAIL) with EDNS enabled. See RFC 6891, Sec. 7, RFC 2671, Sec. 5.3. (140.153.43.44, UDP_-_NOEDNS_)
- nicbr.mil/SOA: No response was received from the server over TCP (tried 3 times). See RFC 1035, Sec. 4.2. (192.82.113.7, TCP_-_EDNS0_4096_D_N)
- nicbr.mil/SOA: The DNSSEC records necessary to validate the response could not be retrieved from the server. See RFC 4035, Sec. 3.1.1, RFC 4035, Sec. 3.1.3. (140.153.43.44, UDP_-_EDNS0_4096_D_KN)
- nicbr.mil/SOA: The response had an invalid RCODE (SERVFAIL) until EDNS was disabled (however, this server appeared to respond legitimately to other queries with EDNS enabled). See RFC 6891, Sec. 6.2.6. (140.153.43.44, UDP_-_EDNS0_4096_D_KN)
- ohtl4mea7p.nicbr.mil/A has errors; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/TXT has errors; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/AAAA has errors; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/A has errors; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/DNSKEY has errors; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/MX has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (16)
- mil to nicbr.mil: The following NS name(s) were found in the delegation NS RRset (i.e., in the mil zone), but not in the authoritative NS RRset: ns03.army.mil See RFC 1034, Sec. 4.2.2.
- mil/DS (alg 8, id 51349): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- mil/DS (alg 8, id 51349): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- mil/DS (alg 8, id 51349): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- mil/DS (alg 8, id 51349): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- nicbr.mil/DS (alg 8, id 50296): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- nicbr.mil/DS (alg 8, id 50296): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- nicbr.mil/DS (alg 8, id 50296): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- nicbr.mil/DS (alg 8, id 50296): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- nicbr.mil/SOA: No response was received until the UDP payload size was decreased, indicating that the server might be attempting to send a payload that exceeds the path maximum transmission unit (PMTU) size. See RFC 6891, Sec. 6.2.6. (192.82.113.7, UDP_-_EDNS0_4096_D_KN, UDP_-_EDNS0_4096_D_KN_0x20)
- ohtl4mea7p.nicbr.mil/A has warnings; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/TXT has warnings; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/CNAME has warnings; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/AAAA has warnings; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/A has warnings; select the "Denial of existence" DNSSEC option to see them.
- nicbr.mil/MX has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.