flowm.daemon.contact
Updated:
2022-06-05 11:24:08 UTC (692 days ago)
Update now
Notices
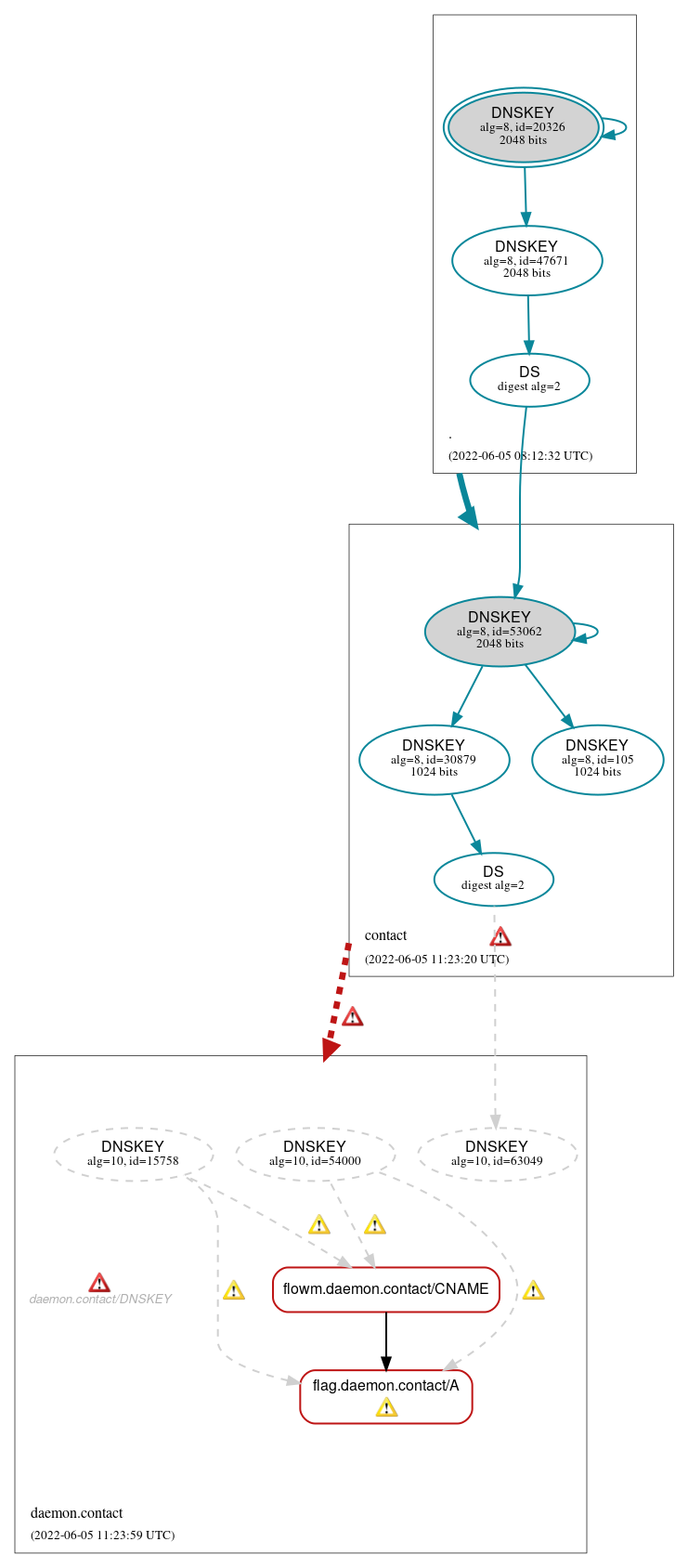
DNSSEC Authentication Chain
 RRset status
RRset status
Bogus (2)
- flag.daemon.contact/A
- flowm.daemon.contact/CNAME
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (7)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 47671)
- contact/DNSKEY (alg 8, id 105)
- contact/DNSKEY (alg 8, id 30879)
- contact/DNSKEY (alg 8, id 53062)
- contact/DS (alg 8, id 53062)
- daemon.contact/DS (alg 10, id 63049)
Non_existent (3)
- daemon.contact/DNSKEY (alg 10, id 15758)
- daemon.contact/DNSKEY (alg 10, id 54000)
- daemon.contact/DNSKEY (alg 10, id 63049)
 Delegation status
Delegation status
Bogus (1)
- contact to daemon.contact
Secure (1)
- . to contact
 Notices
Notices
Errors (5)
- contact to daemon.contact: No valid RRSIGs made by a key corresponding to a DS RR were found covering the DNSKEY RRset, resulting in no secure entry point (SEP) into the zone.
- contact zone: The server(s) were not responsive to queries over UDP. (2a01:8840:f6::34)
- daemon.contact/DNSKEY: No response was received from the server over UDP (tried 12 times). (156.38.157.204, UDP_-_NOEDNS_)
- daemon.contact/DNSKEY: No response was received from the server over UDP (tried 13 times). (195.154.230.217, UDP_-_EDNS0_4096_D)
- daemon.contact/DNSKEY: No response was received from the server over UDP (tried 4 times). (195.154.230.217, UDP_-_EDNS0_512_D_KN)
Warnings (5)
- RRSIG flag.daemon.contact/A alg 10, id 15758: DNSSEC specification recommends not signing with DNSSEC algorithm 10 (RSASHA512).
- RRSIG flag.daemon.contact/A alg 10, id 54000: DNSSEC specification recommends not signing with DNSSEC algorithm 10 (RSASHA512).
- RRSIG flowm.daemon.contact/CNAME alg 10, id 15758: DNSSEC specification recommends not signing with DNSSEC algorithm 10 (RSASHA512).
- RRSIG flowm.daemon.contact/CNAME alg 10, id 54000: DNSSEC specification recommends not signing with DNSSEC algorithm 10 (RSASHA512).
- flag.daemon.contact/A: No response was received from the server over UDP (tried 6 times) until the COOKIE EDNS option was removed (however, this server appeared to respond legitimately to other queries with the COOKIE EDNS option present). (195.154.230.217, UDP_-_EDNS0_4096_D_KN)





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.