_25._tcp.tidamg1.tid.gov.hk
Updated:
2020-03-31 08:53:30 UTC (1720 days ago)
Update now
Notices
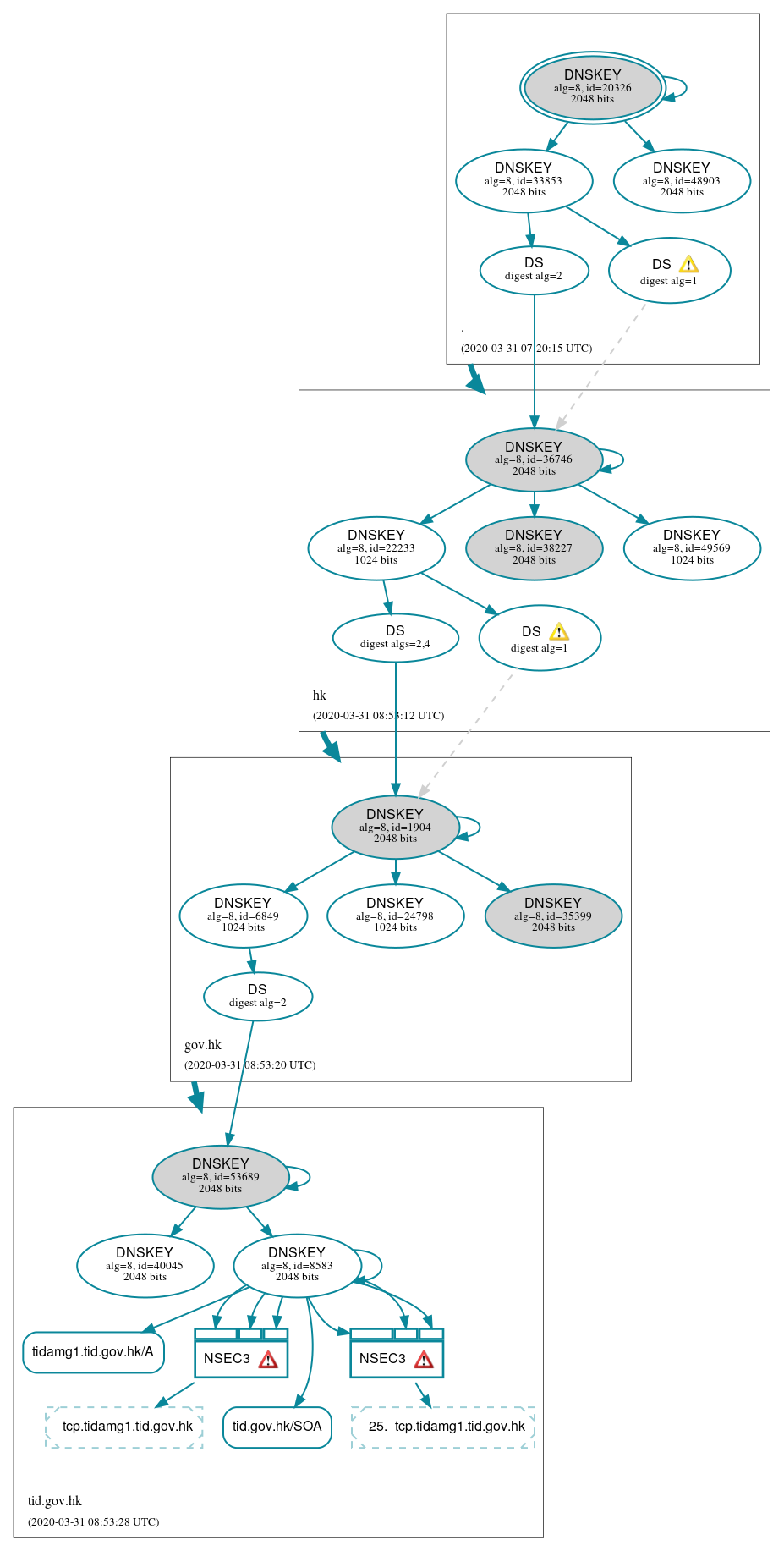
DNSSEC Authentication Chain
 RRset status
RRset status
Secure (4)
- _25._tcp.tidamg1.tid.gov.hk/TLSA (NXDOMAIN)
- _tcp.tidamg1.tid.gov.hk/NS (NXDOMAIN)
- tid.gov.hk/SOA
- tidamg1.tid.gov.hk/A
 DNSKEY/DS/NSEC status
DNSKEY/DS/NSEC status
Secure (21)
- ./DNSKEY (alg 8, id 20326)
- ./DNSKEY (alg 8, id 33853)
- ./DNSKEY (alg 8, id 48903)
- NSEC3 proving non-existence of _25._tcp.tidamg1.tid.gov.hk/TLSA
- NSEC3 proving non-existence of _tcp.tidamg1.tid.gov.hk/NS
- gov.hk/DNSKEY (alg 8, id 1904)
- gov.hk/DNSKEY (alg 8, id 24798)
- gov.hk/DNSKEY (alg 8, id 35399)
- gov.hk/DNSKEY (alg 8, id 6849)
- gov.hk/DS (alg 8, id 1904)
- gov.hk/DS (alg 8, id 1904)
- hk/DNSKEY (alg 8, id 22233)
- hk/DNSKEY (alg 8, id 36746)
- hk/DNSKEY (alg 8, id 38227)
- hk/DNSKEY (alg 8, id 49569)
- hk/DS (alg 8, id 36746)
- hk/DS (alg 8, id 36746)
- tid.gov.hk/DNSKEY (alg 8, id 40045)
- tid.gov.hk/DNSKEY (alg 8, id 53689)
- tid.gov.hk/DNSKEY (alg 8, id 8583)
- tid.gov.hk/DS (alg 8, id 53689)
 Delegation status
Delegation status
Secure (3)
- . to hk
- gov.hk to tid.gov.hk
- hk to gov.hk
 Notices
Notices
Errors (5)
- NSEC3 proving non-existence of _25._tcp.tidamg1.tid.gov.hk/TLSA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of _25._tcp.tidamg1.tid.gov.hk/TLSA: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of _tcp.tidamg1.tid.gov.hk/NS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of _tcp.tidamg1.tid.gov.hk/NS: An iterations count of 0 must be used in NSEC3 records to alleviate computational burdens. See RFC 9276, Sec. 3.1.
- tid.gov.hk/CNAME has errors; select the "Denial of existence" DNSSEC option to see them.
Warnings (15)
- NSEC3 proving non-existence of _25._tcp.tidamg1.tid.gov.hk/TLSA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of _25._tcp.tidamg1.tid.gov.hk/TLSA: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of _tcp.tidamg1.tid.gov.hk/NS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- NSEC3 proving non-existence of _tcp.tidamg1.tid.gov.hk/NS: The salt value for an NSEC3 record should be empty. See RFC 9276, Sec. 3.1.
- gov.hk/DS (alg 8, id 1904): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- gov.hk/DS (alg 8, id 1904): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- gov.hk/DS (alg 8, id 1904): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- gov.hk/DS (alg 8, id 1904): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- gov.hk/DS (alg 8, id 1904): In the spirit of RFC 4509, DS records with digest type 1 (SHA-1) might be ignored when DS records with digest type 4 (SHA-384) exist in the same RRset. See RFC 4509, Sec. 3.
- gov.hk/DS (alg 8, id 1904): In the spirit of RFC 4509, DS records with digest type 1 (SHA-1) might be ignored when DS records with digest type 4 (SHA-384) exist in the same RRset. See RFC 4509, Sec. 3.
- hk/DS (alg 8, id 36746): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- hk/DS (alg 8, id 36746): DNSSEC implementers are prohibited from implementing signing with DS algorithm 1 (SHA-1). See RFC 8624, Sec. 3.2.
- hk/DS (alg 8, id 36746): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- hk/DS (alg 8, id 36746): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. See RFC 4509, Sec. 3.
- tid.gov.hk/CNAME has warnings; select the "Denial of existence" DNSSEC option to see them.





 JavaScript is required to make the graph below interactive.
JavaScript is required to make the graph below interactive.